Authorization Boundary Diagram¶
An Authorization Boundary Diagram is a visual presentation of your software components and data connections.
The Game Warden team requires that you provide this diagram so we may understand your system design and ensure it properly connects to our environment. For example, we need to know your external data connections and similar components.
When establishing external data connections, it is imperative that you have a complete understanding of your data directional flow:
- Egress – Data leaves or exits the Game Warden boundary.
- Ingress – Data enters the Game Warden boundary.
- Bidirectional – Data leaves and enters the Game Warden boundary.
The external data connections are critical because data must be transmitted to your application via the Internet. The Game Warden team needs to fully understand the ports in use, and how they manage data (ingress or egress) such that there is no data spillage; for example, IL4+ data cannot exist at a lower Impact Level. For any applications accredited at IL4+, data transit across Game Warden boundary (to/from applications) must align with government requirements. Therefore, we must see these connections on your diagrams.
In previous years, our team requested that you create and provide an architecture design. Subsequent to that time, we requested that you create and provide an Authorization Boundary Diagram. This current request combines the two, though still using the name: Authorization Boundary Diagram.
An Authorization Boundary Diagram not only helps the Game Warden team see data leaving the boundary but also allows us to view all physical components of your system.
The content below proactively provides guidance on the requirements for your Game Warden Authorization Boundary Diagram. Aligning your diagram with the specifications below ensures compliance with Authority to Operate (ATO) requirements.
When creating your diagram, you must display all data movement both within your application and outside this boundary. This includes specifications that describe which direction the data moves, such as ingress, egress, or bidirectional. You must denote the ports and protocols on all connections. You also must display all application containers and all external or managed services.
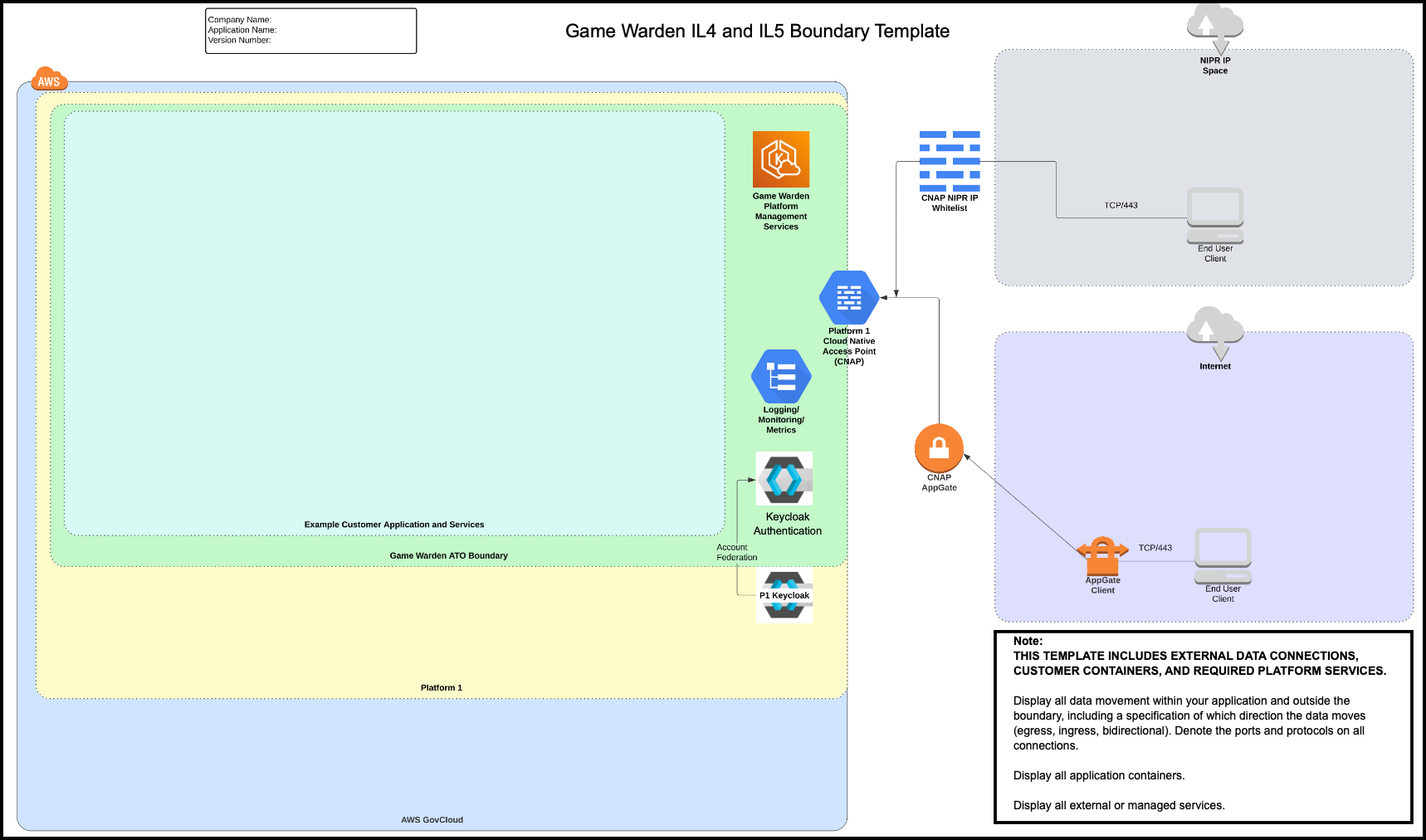
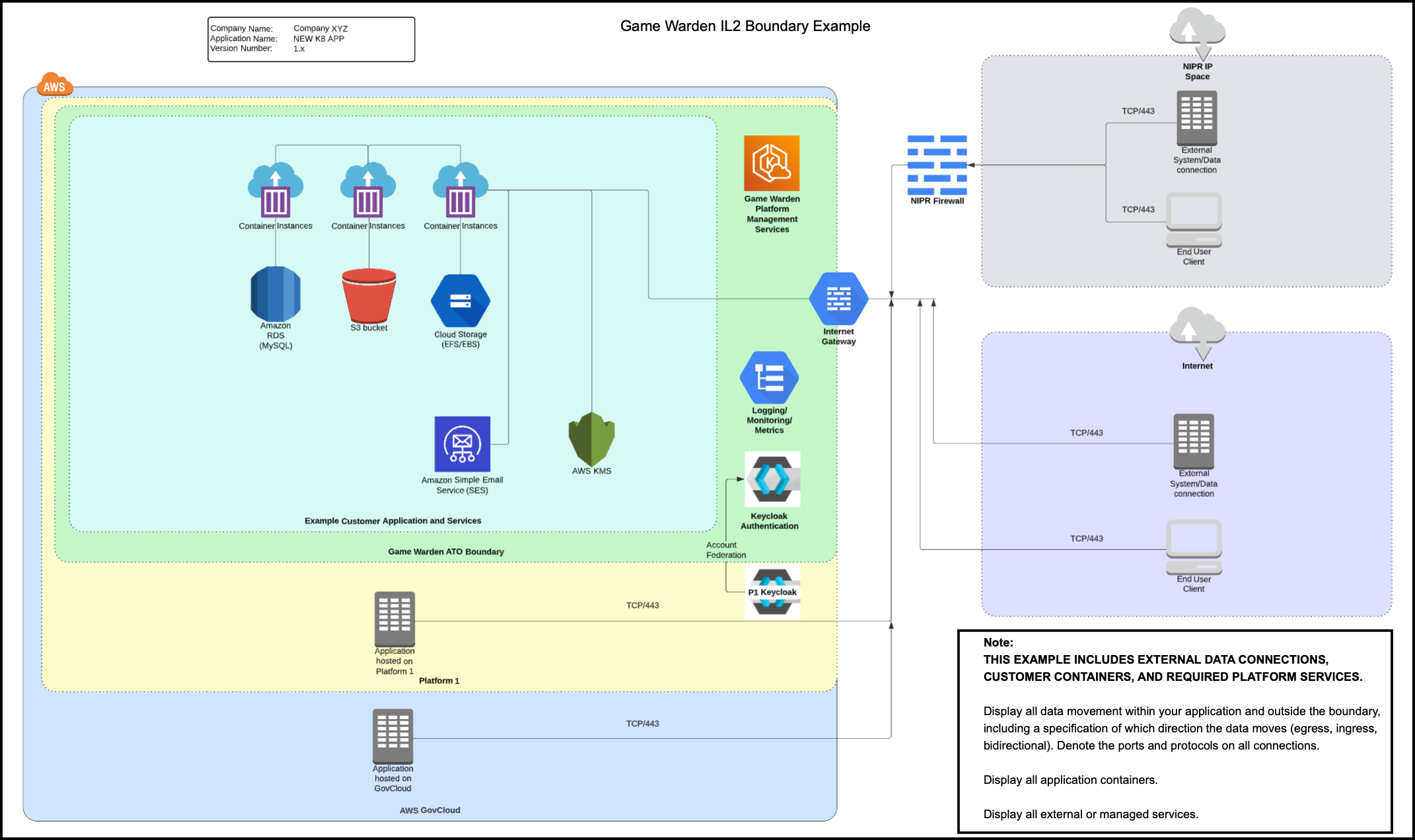
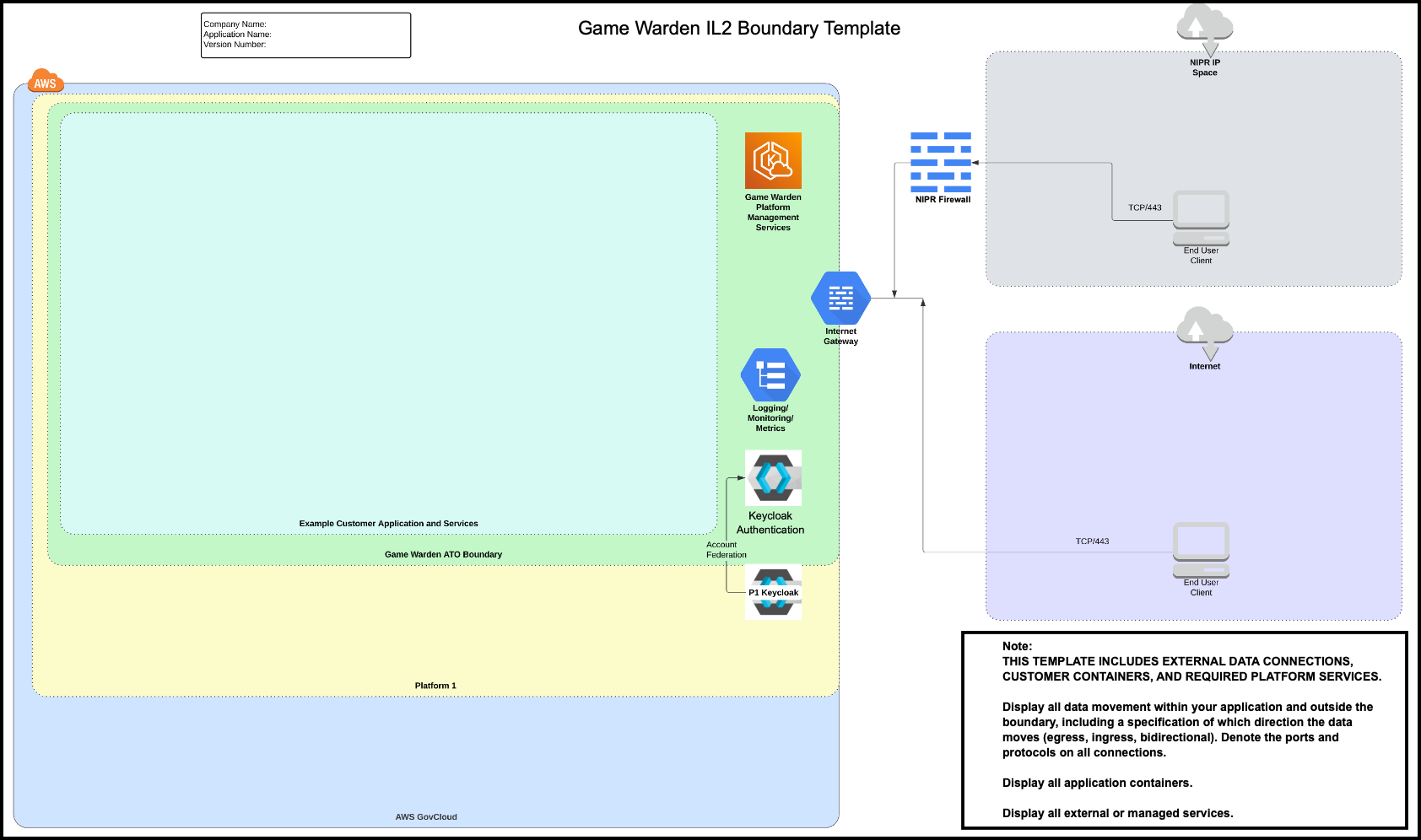
In the images below, the right side of the diagram displays two end users accessing the Game Warden environment; one using the Department of Defense (DoD) Non-classified Internet Protocol Router Network (NIPRNet) IP, and the other using public Internet. The DoD uses NIPRNet to manage unclassified information.
The Cloud Native Access Point (CNAP) only exists at IL4 and IL5. In the diagrams below, the primary distinction between IL2 and IL4-IL5 is CNAP or an Internet Gateway. CNAP NIPR IP Whitelist screens the NIPR IP user, based on an allowable list of IP addresses. Both users proceed through an Internet Gateway to the Game Warden ATO Boundary, gaining access to AWS services and container instances. All customer environments are Keycloak-protected areas. For Platform One (P1)-hosted applications, you must provide P1 login credentials. CNAP functions as the P1 gatekeeper.
As evident in the diagrams, the data access methods include:
- NIPRNet
- Public Internet
- Platform One
- AWS GovCloud
IL2 Boundary Diagram Example¶
The diagram below displays the external data connections, customer containers, and the required platform services.
IL2 Boundary Template¶
Below is the corresponding template that you can use as a guide to create your IL2 Authorization Boundary Diagram. You can access an editable template in an MS Visio (VSDX) format, which will be made available to you on the Documents page of the Game Warden Web App.
IL4/IL5 Boundary Diagram Example¶
The diagram below displays the external data connections, customer containers, and the required platform services.
Note
If your Virtual Desktop Infrastructure (VDI) is within NIPRNet, you can access IL4 and IL5 without using Appgate SDP which is a DoD-approved authentication service. The DoD's P1 team requires that you use Appgate SDP if you do not use NIPRNet or NIPRNet VPN (such as Air Force Desktop Anywhere), as you cannot access IL4 or IL5 without using one of these options. For additional information, read Appgate.
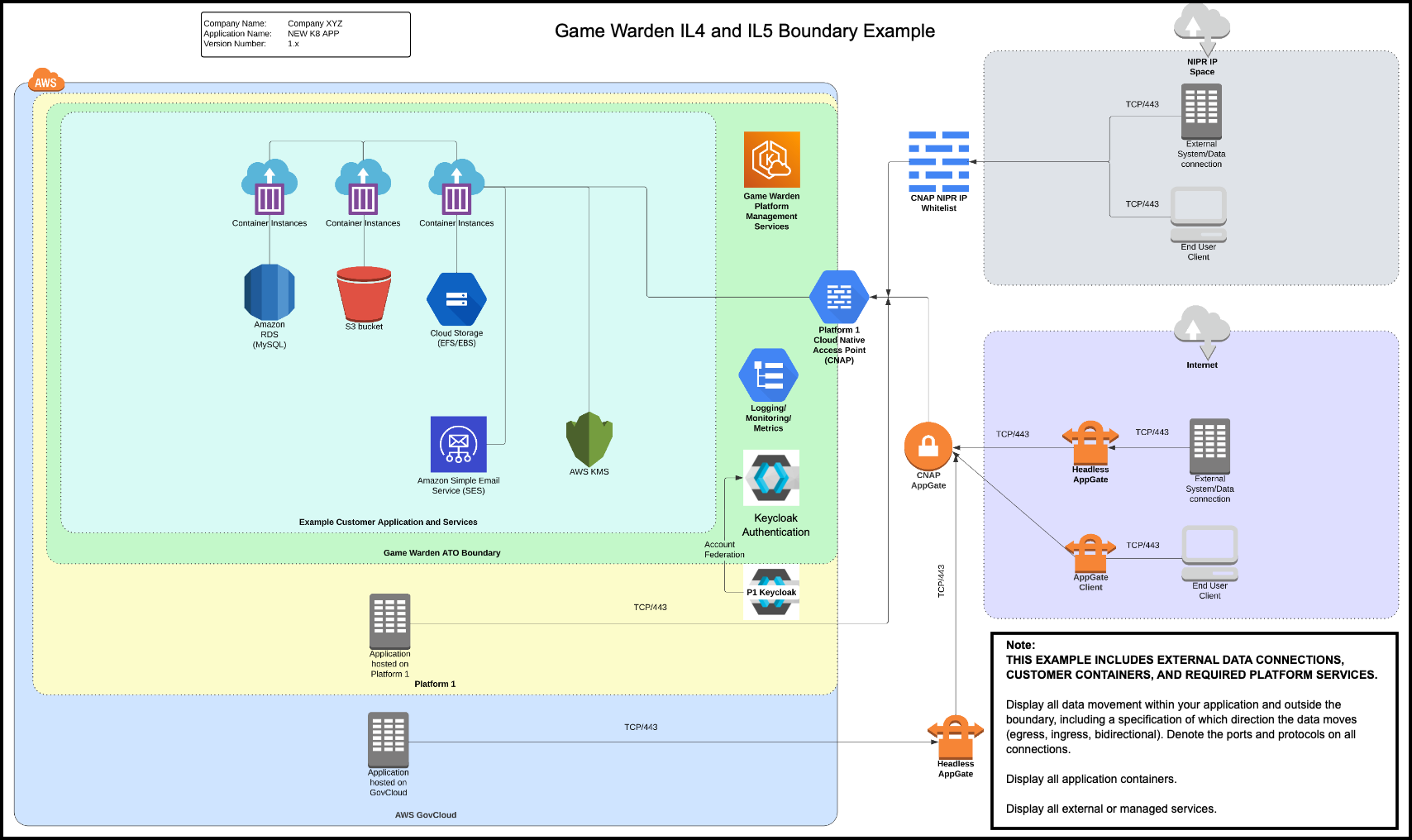
IL4/IL5 Boundary Template¶
Below is the corresponding template that you can use as a guide to create your IL4/IL5 Authorization Boundary Diagram. You can access an editable template in an MS Visio (VSDX) format, which will be made available to you on the Documents page of the Game Warden Web App.