Recommended Containers¶
Your application must be containerized to deploy on the Game Warden platform. Your team is free to utilize whichever container tools you prefer; however, Game Warden recommends the following options to significantly simplify the onboarding of your application to the Game Warden platform:
Chainguard Containers - While there are fewer image container options available from Chainguard, we recommend checking their inventory first before moving to Iron Bank’s container options.
Iron Bank Containers - These containers have been scanned by Platform One and offer a number of options to application developers.
Build your own/find other options - You can build your own containers or find options other than Chainguard or Iron Bank. We recommend Chainguard and Iron Bank for their security compliance which helps mitigate Common Vulnerabilities and Exposures (CVEs) unearthed by our security scanning tools. - If you opt for this third option, we recommend utilizing the free, open-source scanning tools Trivy and Grype to get a sense of CVEs your team will need to resolve.
Chainguard Containers¶
Chainguard is a “collection of container images designed for security and minimalism” and is a good alternative to Iron Bank base images. The primary advantage of Changuard images are their reduced size and complexity, generally resulting in zero Common Vulnerabilities and Exposures.
Learn more about Chainguard images here.
Your team can build upon Chainguard base images and push them (instructions here) to the Game Warden Harbor repository.
If you use a Chainguard image with the latest tag, it is free. They do support older versions of these images but using them will incur an expense.
Precautions
- Chainguard images are free only if they have the
latesttag. - Chainguard will always label their newest images with the
latesttag, so if you have automation established to always pull the image with thelatesttag into Game Warden, be aware that updates in the image could disrupt your application’s functionality. - This can be avoided by pulling the image and tagging it with your app version before pushing to Game Warden.
Iron Bank Containers¶
Iron Bank is a registry that stores containerized images that have been scanned by Platform One (P1) and align with Department of Defense (DoD) standards. These images can be pushed to Harbor (instructions here), our secure registry, and eventually deployed to Game Warden.
An Iron Bank container can either be compliant or non-compliant with the Acceptance Baseline Criteria (ABC). There is also an Overall Risk Assessment (ORA) score; 100% is the best, and 0% the worst.
Example:


With coordination among Platform 1 (P1), the government-designated Game Warden Information Systems Security Manager (ISSM), and the Second Front Systems (2F) Security team, each container will be assessed for approval on the Game Warden platform. This process gives 2F flexibility to assess and accept the risk of application containers.
Iron Bank Image Usage and Responsibilities¶
It is your team’s responsibility to understand the Acceptance Baseline Criteria (ABC) compliance and Overall Risk Assessment (ORA) rating of your Iron Bank containers.
Containers with the following ratings in Iron Bank will have the highest probability of being approved for use on the Game Warden platform:
- Acceptance Baseline Criteria: Compliant
- ORA score: 80% or greater.
If an Iron Bank container does not initially satisfy the security requirements, you may be required to select a different image. Containers that do not meet this threshold might still be approved after being reviewed by the Game Warden Security team. Low and Medium CVEs over the threshold may be justified. Critical and High CVEs will be evaluated on a case-by-case basis to determine the security impact.
Containers may become non-compliant and/or receive a lower ORA score at any time when Common Vulnerabilities and Exposures (CVEs) exceed the timeline requirements. To help with this uncertainty, please notify 2F of any Iron Bank containers you plan to use that are currently shown as compliant and have a good ORA score. The Game Warden team will do its best to support their use.
When image compliance changes, your team must coordinate with the image owner, through P1, to resolve the issue. As an alternative, you can migrate to an acceptable image; preferably, this would be an updated and compliant image. If the Iron Bank base image becomes non-compliant due to End of Life (EoL), for example, you should switch to an updated base image with an appropriate ABC criteria and ORA score.
Typically, there is a substantial overlap (such as 6-12 months) between when a new base image is introduced and when the previous version becomes EoL. As a best practice, application developers should check for updated image versions monthly (at minimum) and transition to the new releases. This will improve application security and ensure government compliance.
FAQ: What is End of Life (EoL)?
A container with an End of Life designation will no longer be supported or updated by the image owner. Iron Bank containers marked EoL are less likely to be approved for Game Warden platform deployments.
The image below displays an example container which has been marked EoL.
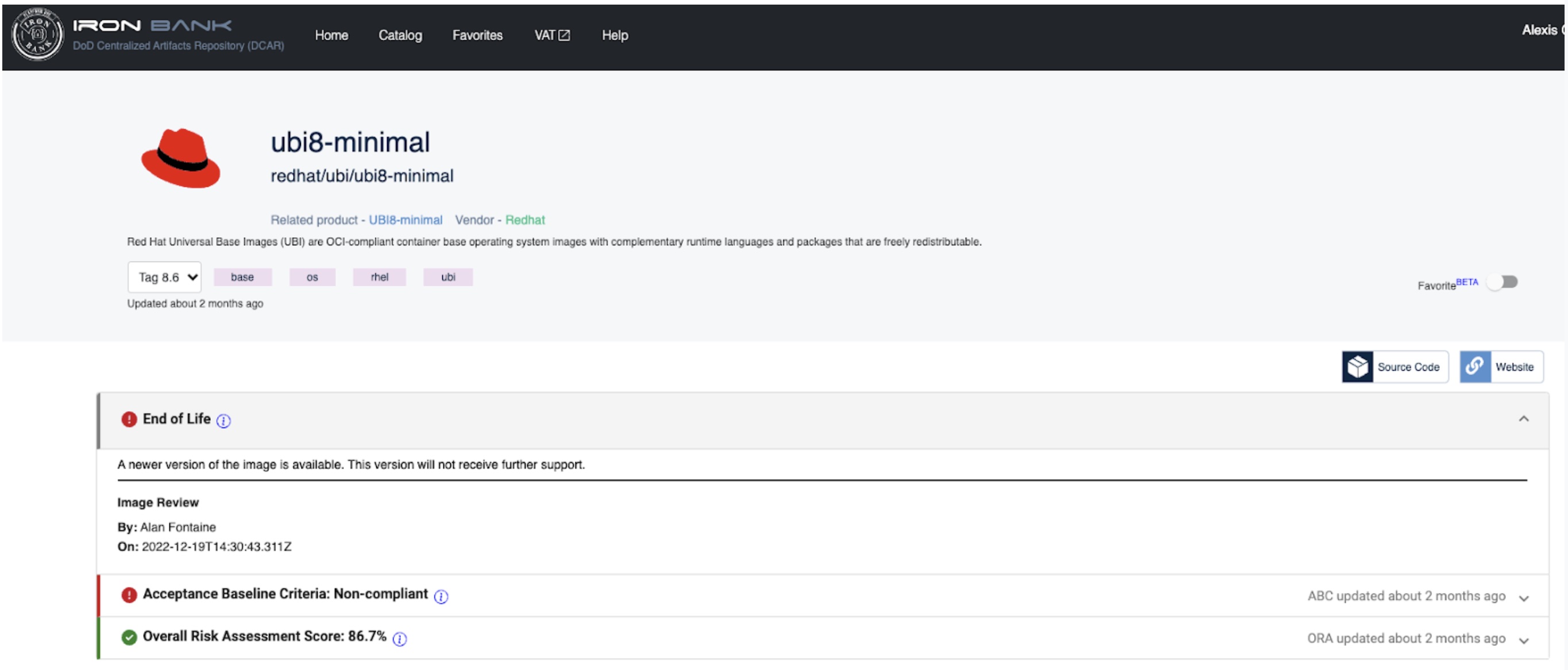
Iron Bank Container Approval in Game Warden¶
2F may approve unmodified container images that are ABC compliant or meet acceptable risk levels. It is the responsibility of the application developer to use the latest approved images; this ensures the image remains compliant and has the latest (or most current) security updates.
Using the Iron Bank UI, search for the image you would like to use; the latest or most current image appears first. All available images should populate, and you can use the tag drop-down menu to switch between different image versions.
The 2F Security team will review container scans and inherit any artifacts found in the selected container. Game Warden customers will notify the 2F Security team when a new base image is used prior to uploading to the 2F Harbor Repository. When an Iron Bank image is approved for use in Game Warden, the approved vulnerability justifications for the base image will be shown as inherited in Game Warden Scan Lab and in the Deployment Passport; therefore, these vulnerabilities will not require further effort from the application developer.
The Game Warden Scan Lab image below displays examples of Inherited from Base Image justifications.
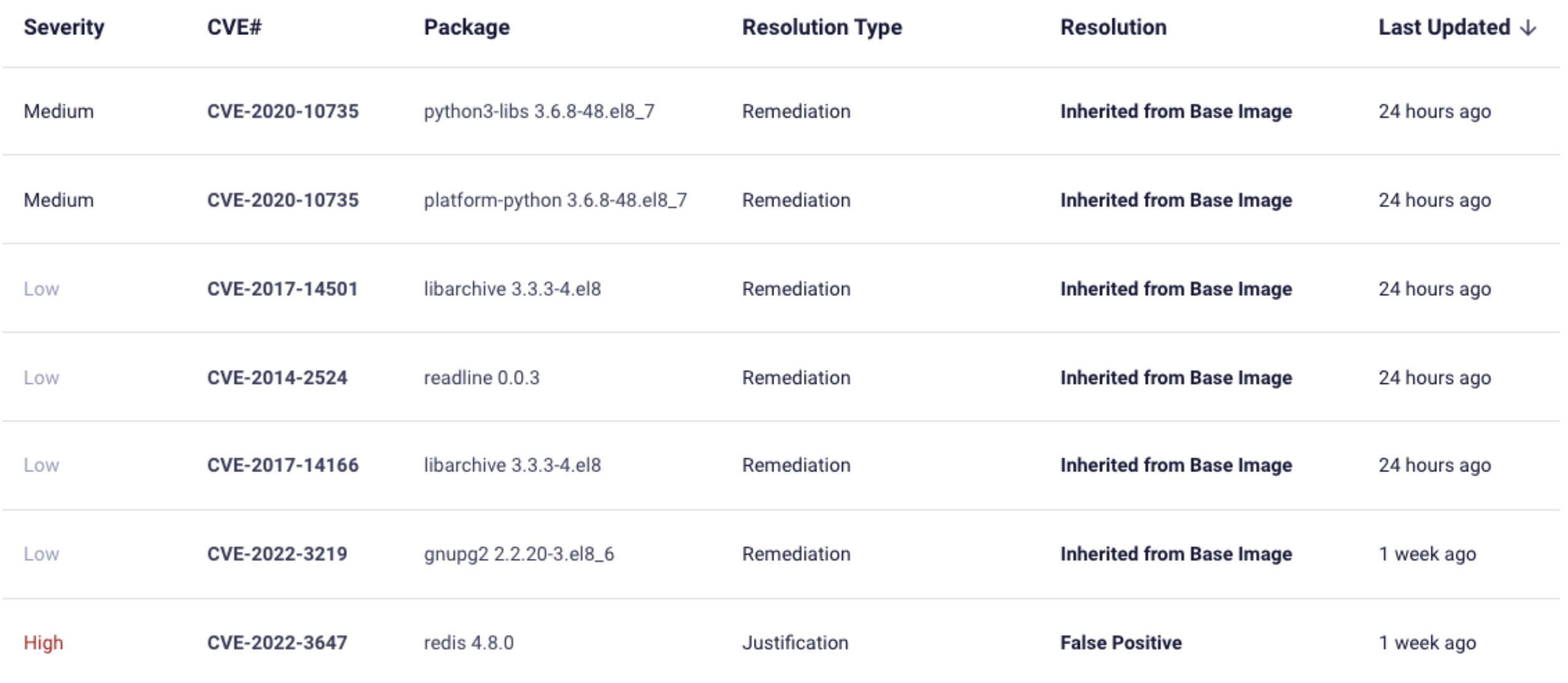
If a specific image is selected and is comprised of multiple layers, it is possible for the 2F Security team to review the selected container to determine if base layer vulnerabilities can be Inherited from Base Image.
GW Assessment Example
You would like to use a Postgresql11 image that is “Non-compliant” and has an ORA score of 26%. The vulnerabilities in the “Postgresql11” layer are the reason why this container is receiving said scores. You can request that the 2F Security team review this container. When the 2F Security team reviews the “Postgresql11” container, the team finds that the base layer of “Postgresql11” is the latest version of UBI9. UBI9 is “Compliant” and has an ORA score of 85%. Since the base layer of the “Postgresql11” container meets acceptable risk levels, the 2F Security team is able to “Inherit” justifications from ONLY the Iron Bank UBI9 base layer. You must remediate (own) the vulnerabilities included in the Postgresql11 layer.
Pulling Containers from Iron Bank¶
To pull containers from Iron Bank (or if your application is not built on an Iron Bank-approved base image):
- Log in to the Iron Bank Hardened Containers Catalog.
You will need to create a Platform One SSO if you do not have this credential. -
Use Search to locate your preferred image in the Catalog.
-
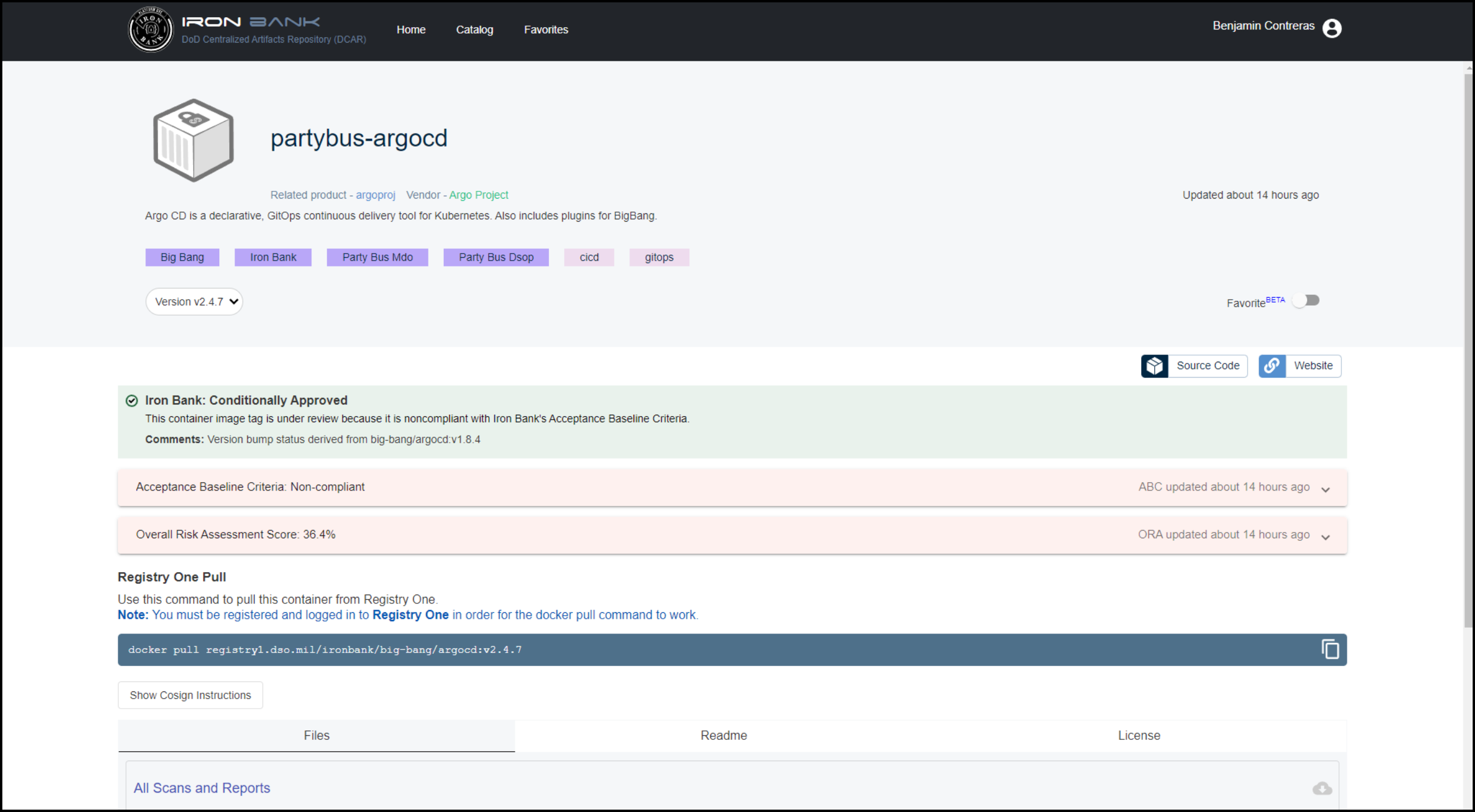
Click this image to access the Registry One Docker Pull Command.
In the example below, the Docker pull command appears as:
docker pull registry1.dso.mil/ironbank/big-bang/argocd:v2.4.7`
Note
You must be registered and logged in to Registry One for the Docker pull command to work.
Other Considerations¶
Where possible, the Game Warden team recommends utilizing distroless containers. Distroless containers provide a number of benefits for your applications and deployments:
-
Smaller size resulting in reduced download times and lower costs
-
Enhanced security due to minimized attack surfaces, fewer dependencies, and fewer vulnerabilities
-
Simplified management to include easier debugging, reduced build complexity, and improved portability
Last Updated: 01/05/2023