Scan Lab Overview¶
Scan Lab, accessible via App Central, allows you to view, resolve or justify Common Vulnerabilities and Exposures (CVEs), address Anchore compliance results, and access the Security team's responses to proposed resolutions.
Once you are granted access to your Harbor repository, you can begin pushing your containerized images. Our pipelines will automatically scan these images using integrated security tools and populate Scan Lab with the results.
Scan time varies depending on the size and complexity of the image. If results do not appear in Scan Lab after pushing your image, please notify our team by submitting a Support Ticket.
Review scan results in Scan Lab¶
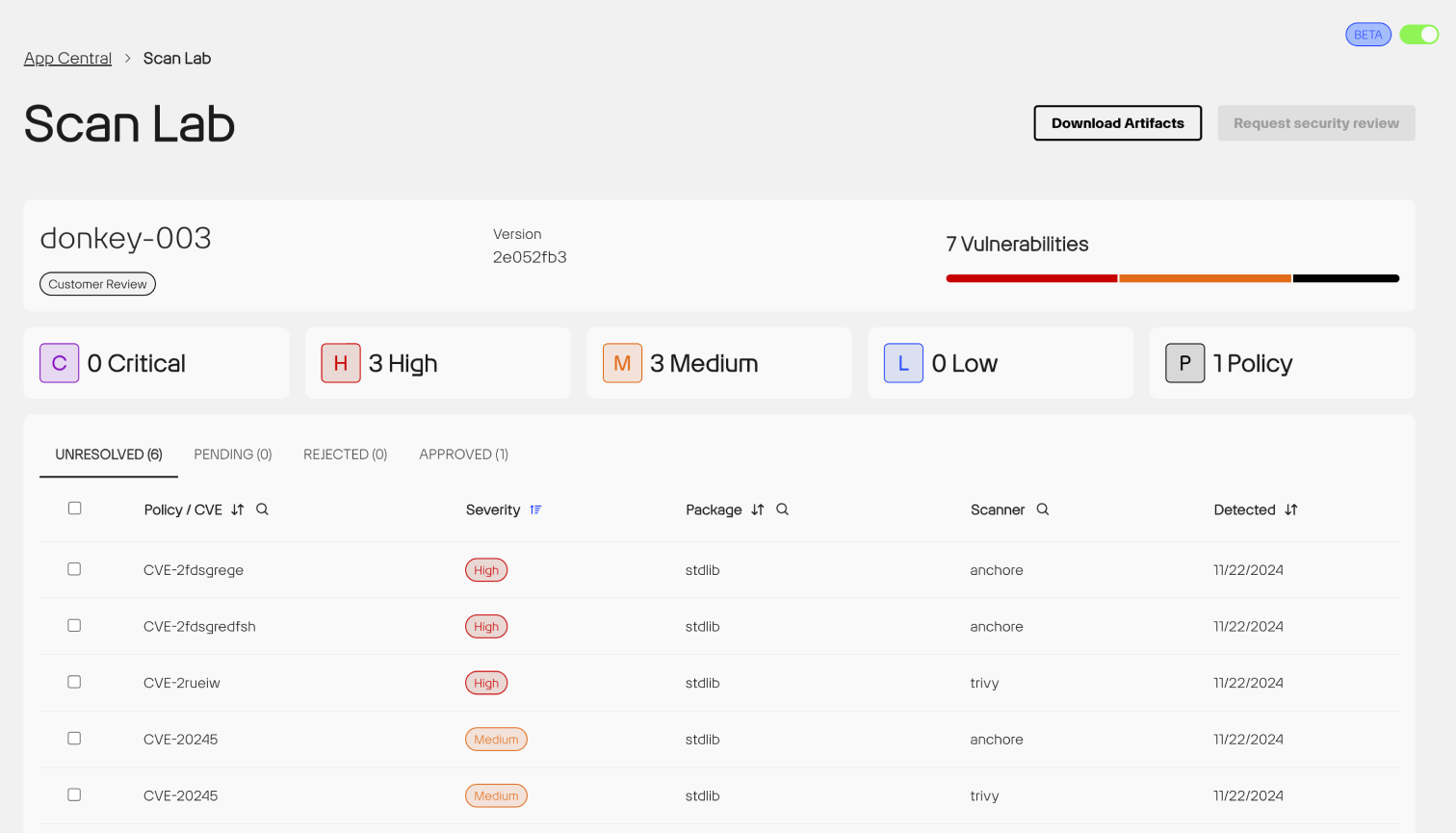
Services are organized by their hosted environments, such as Development, Staging, and Production. Use the toggle to display the list of services within each environment. From there, you can review a service’s scan results in Scan Lab by clicking its entry in the Vulnerabilities column.
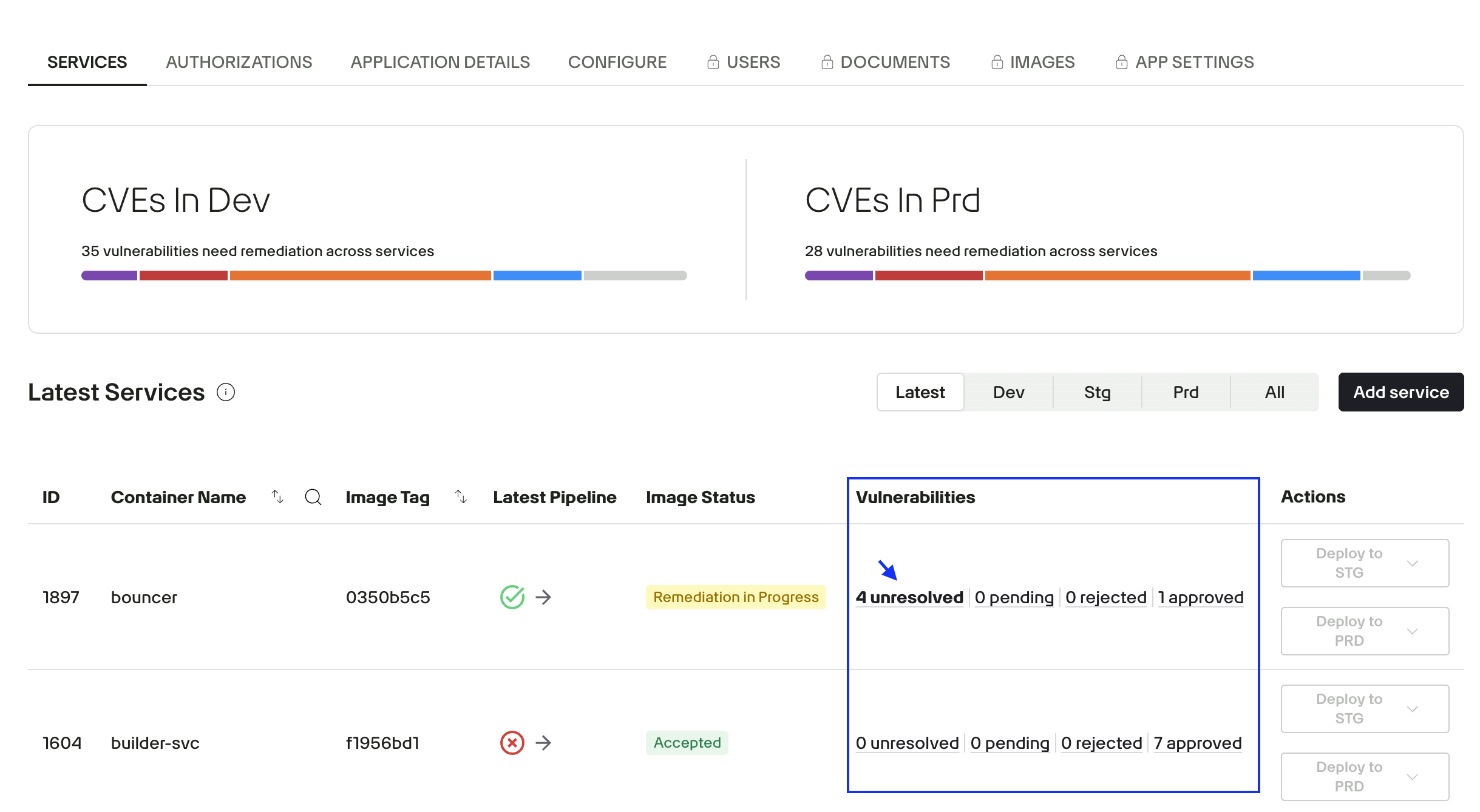
On the Scan Lab page, information is organized to help you focus on CVEs and identify the top vulnerability priorities for your application. Each application package has its own Scan Lab view with corresponding scan results.
Severity status hierarchy¶
Vulnerabilities are categorized by severity using industry-standard scoring:
| Severity | Description |
|---|---|
| Critical | Immediate remediation required. These could be exploitable remotely and have high impact. |
| High | Should be addressed quickly but may not pose as severe a risk as Critical. |
| Medium | Important to fix, but not an urgent blocker. |
| Low | Minor issues or informational findings. |
| Policy | Issues that violate platform-defined Anchore compliance policies. |
Resolution tracking¶
Each vulnerability will be assigned one of the following statuses, allowing for clear tracking of progress and decisions:
| Status | Description |
|---|---|
| Unresolved | No action taken yet. |
| Pending | Justification submitted, awaiting review from Security. |
| Rejected | Justification denied; remediation is required. |
| Approved | Justification accepted; no further action needed. |
Bulk actions for justifications¶
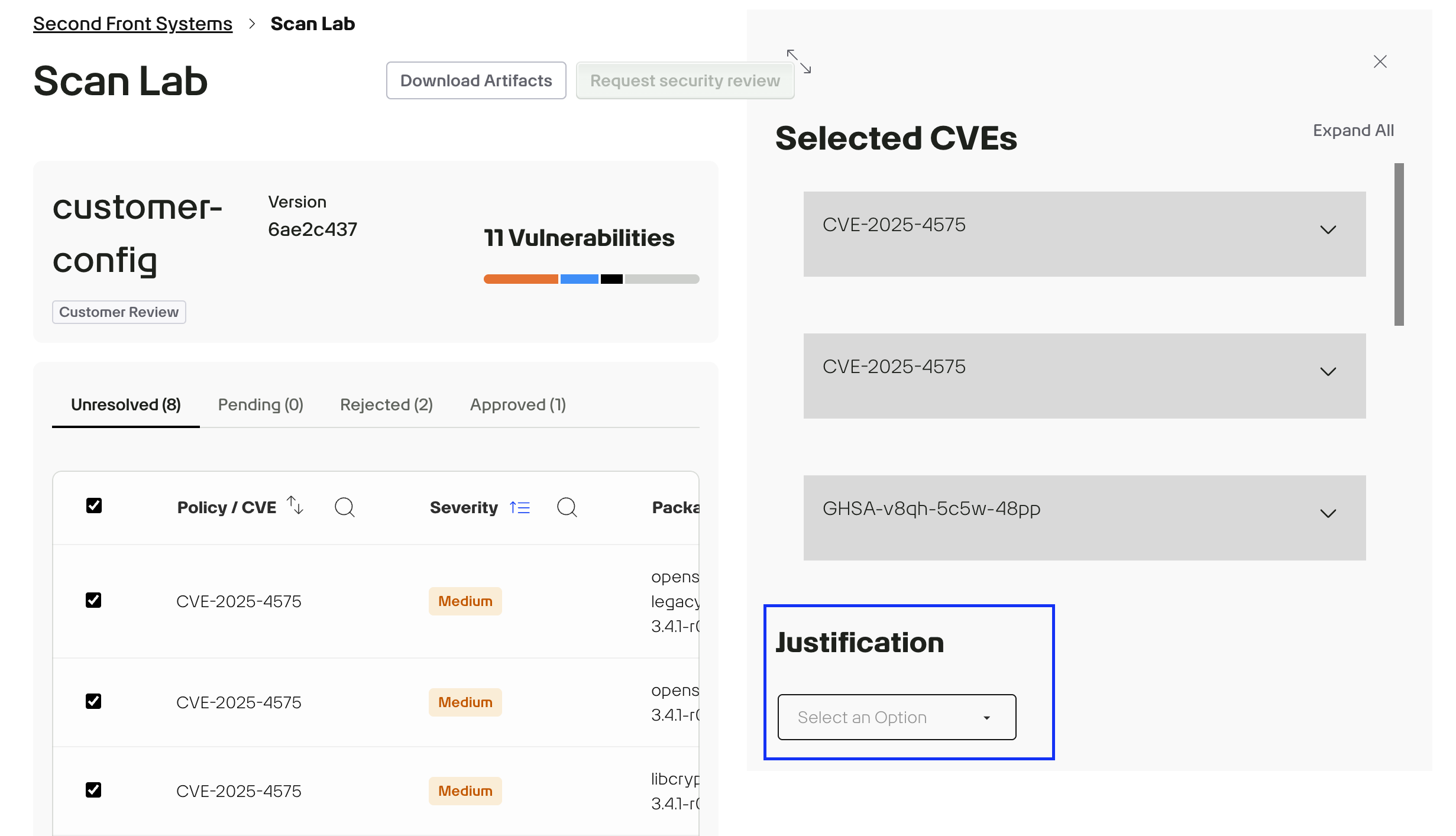
For services in the Development environment, you can select multiple packages at once and apply a single justification to address the same vulnerability across all selected packages. This streamlines the process when multiple components share a common issue and resolution rationale.
Warning
- To submit your resolutions to the Game Warden team, you must address all security findings for your image.
- Once all findings have been resolved or properly justified, click the Ask for security review button to send a review request. The Game Warden Security team will review your submissions and either approve or deny your proposed resolutions.
Downloading artifacts¶
Click the Download Artifacts button in the upper-right corner of Scan Lab to download your raw scan data and Software Bill of Materials (SBOM). This makes it easier to share information or work offline.
Production image scanning¶
Game Warden performs automated vulnerability scans on all customer-deployed production container images on the first calendar day of each month. This recurring scan schedule ensures that newly disclosed vulnerabilities are detected and surfaced in a timely manner.
When vulnerabilities are identified, your team will receive notifications through both Slack and the Game Warden App. These alerts enable prompt triage and resolution of security findings.
CVE due dates
- CVE remediation deadlines are enforced only after your application has been deployed to a production environment. Each CVE includes a due date for remediation or justification. This date aligns with the Remediation/Justification timeline specified in Table A of the Game Warden Acceptance Baseline Criteria.
- Your team is responsible for either resolving the CVE or submitting an acceptable justification by the stated deadline.