Chainguard & Iron Bank Imaging¶
With coordination among Platform 1 (P1), the government-designated Game Warden Information Systems Security Manager (ISSM), and the Second Front Systems (2F) Security team, each container will be assessed for approval on the Game Warden platform. This process gives 2F flexibility to assess and accept the risk of application containers.
Containerization and Imaging¶
Your application must be containerized to deploy on the Game Warden platform. Your team is free to utilize whichever container tools you prefer; however, Game Warden recommends the following options to significantly simplify the onboarding of your application to the Game Warden platform:
Chainguard Containers
- While there are fewer image container options available from Chainguard, we recommend checking their inventory first before moving to Iron Bank’s container options.
Iron Bank Containers
- These containers have been scanned by Platform One and offer a number of options to application developers.
Build your own/find other options
-
You can build your own containers or find options other than Chainguard or Iron Bank. We recommend Chainguard and Iron Bank for their security compliance which helps mitigate Common Vulnerabilities and Exposures (CVEs) unearthed by our security scanning tools.
-
If you opt for this third option, we recommend utilizing the free, open-source scanning tools Trivy and Grype to get a sense of CVEs your team will need to resolve.
Note
Critical and High CVEs will be evaluated on a case-by-case basis to determine the security impact. Low and Medium CVEs over the threshold should always be considered for remediation as a priority. A CVE Memo is required for any justification needs, alternatively.
Distroless Images¶
Chainguard and Iron Bank offer a collection of container images that includes both distroless and development images. Distroless images are designed to be minimal and only contain the software needed to run an application or service. They don't include a shell or package manager, and are built using Wolfi, a Linux undistro designed for the cloud-native era.
Where possible, the Game Warden team recommends utilizing distroless containers. Distroless containers provide a number of benefits for your applications and deployments:
-
Smaller size resulting in reduced download times and lower costs
-
Enhanced security due to minimized attack surfaces, fewer dependencies, and fewer vulnerabilities
-
Simplified management to include easier debugging, reduced build complexity, and improved portability
Chainguard Containers¶
Chainguard is a collection of container images designed for security and minimalism, and is a good alternative to Iron Bank base images. The primary advantage of Changuard images are their reduced size and complexity, generally resulting in zero Common Vulnerabilities and Exposures. Your team can build upon Chainguard base images and push them to the Game Warden Harbor repository. If you use a Chainguard image with the latest tag, it is free. They do support older versions of these images but using them will incur an expense.
Pulling Chainguard Images¶
You can access Images directly from the Chainguard Registry. The Chainguard Registry provides public access to all public Chainguard Images, and provides customer access for Production Images after logging in and authenticating.
Info
There are two different tracks of Chainguard Images: Production Images and Developer Images. Developer Images are publicly available and free to use by anyone. Developer Images always represent images tagged with :latest or :latest-dev. Production Images are enterprise-ready images that come with patch SLAs and features such as Federal Information Processing Standard (FIPS) readiness and unique time stamped tags. There are also specific major and minor versions of open source software available as Production Images.
You can find complete lists of all the Developer and Production Images available to you in the Chainguard Console. After logging in, you will be able to find all the current Developer Images in the 'Public images' tab. If you’ve selected an appropriate Organization in the drop-down menu above the left hand navigation, you can find your organization’s Production Images in the 'Organization images' tab.
Note
Specific package versions can be made available in Production Images. If you have a request for a specific package version, please contact Chainguard support.
Info
Learn more about Chainguard images here.
!!! warning "Precautions'' Chainguard images are free only if they have the latest tag. Chainguard will always label their newest images with the latest tag, so if you have automation established to always pull the image with the latest tag into Game Warden, be aware that updates in the image could disrupt your application’s functionality. This can be avoided by pulling the image and tagging it with your app version before pushing to Game Warden. - If you need to use an image that is not offered for free, please reach out to your TIM or CSM to learn more about our partnership with Chainguard.
Chainguard Frequently Asked Questions¶
What does 2F’s partnership with Chainguard mean for me?
There are two key benefits for Second Front customers: discounted pricing and ease of access to images.
Second Front Systems has negotiated significantly discounted rates on Chainguard images for our customers. We also have a registry powered by Chainguard, so you’ll be able to easily access your Chainguard images.
What should I do if I want to learn more?
Reach out to your Customer Success Manager (CSM)!
It’s important to go through your CSM and not direct to Chainguard. Since these discounts are for Second Front customers only, we have a formal registration process that kicks off when you engage your CSM. This will help Chainguard properly track that you’re a Game Warden customer and expedite your sales process with Chainguard.
What are each team’s roles for the Chainguard billing process?
Once you let your Customer Success Manager know you’re interested, we’ll connect you with a Chainguard sales representative. The sales process is between you and Chainguard. You are agreeing to their terms and payment is between your two teams. Once you’ve closed with Chainguard, the Second Front team steps in to get you access to your new Chainguard images.
Who do I reach out to if I have issues with my image?
The Second Front team is here to help you access your Chainguard images. If there’s a problem with your image, create a ticket with Second Front so we can look into it internally first. If needed, we’ll work with you to engage Chainguard support.
How do I engage Chainguard support?
If you want to engage Chainguard support, you’ll need a login. Let your Customer Success Manager know you’d like one and we can request account creation with the Chainguard team. You’ll receive email notification that your account has been created and you’ll be able to login and submit a ticket.
Which images can I purchase from Chainguard?
Chainguard maintains hundreds of images. You can search for your image of interest here.
What if I don’t see the image I need?
Chainguard is constantly adding new images to their library. If you don’t see an image you need, let your CSM know. If it’s an open source image that Chainguard can support, Chainguard can build it for you in a matter of weeks.
Why would I pay for Chainguard images if there are free images available?
Free Chainguard images are a great resource to explore how to engage with their solution. However, Chainguard does not recommend using their free images for software deploying to production environments. Free images require using the “latest” tag, so are updated frequently and without notice.
Over time, Chainguard is phasing out their free images and many of their images will not have a free option available.
How can I be confident the image won’t have vulnerabilities?
Search for the image you need here.
Once you find the image, click on the latest version. A side navigation will open on the left of your screen and you can click “Vulnerabilities” tab to see if there are any known CVEs.
How often are Chainguard images updated?
Chainguard images are maintained by the Chainguard team and updates are pushed twice daily. Second Front’s registry syncs with these update times, so your images are updated in near real-time.
Who is responsible for addressing vulnerabilities in an image?
Chainguard images are no-to-low CVEs. Chainguard will help you address a vulnerability (provide appropriate justification, etc.) if it’s a known vulnerability in their image. In most cases, you will see zero vulnerabilities in Chainguard images.
If you build on top of or add software to an image, you (not Second Front or Chainguard) are responsible for any CVEs that exist.
Iron Bank Containers¶
Iron Bank is a registry that stores containerized images that have been scanned by Platform One (P1) and align with Department of Defense (DoD) standards. These images can be pushed to Harbor (instructions here), our secure registry, and eventually deployed to Game Warden.
An Iron Bank container can either be compliant or non-compliant with the Acceptance Baseline Criteria. There is also an Overall Risk Assessment score; 100% is the best, and 0% the worst.
Example:


Iron Bank Image Usage and Responsibilities¶
Warning
It is your team’s responsibility to understand the Acceptance Baseline Criteria compliance and Overall Risk Assessment rating of your Iron Bank containers.
Containers with the following ratings in Iron Bank will have the highest probability of being approved for use on the Game Warden platform:
-
Acceptance Baseline Criteria: Compliant
-
Overall Risk Assessment score: 80% or greater.
If an Iron Bank container does not initially satisfy the security requirements, you may be required to select a different image. Containers that do not meet this threshold might still be approved after being reviewed by the Game Warden Security team.
Warning
Containers may become non-compliant and/or receive a lower Overall Risk Assessment score at any time when Common Vulnerabilities and Exposures (CVEs) exceed the timeline requirements. To help with this uncertainty, please notify 2F of any Iron Bank containers you plan to use that are currently shown as compliant and have a good Overall Risk Assessment score. The Game Warden team will do its best to support their use.
When image compliance changes, your team must coordinate with the image owner, through P1, to resolve the issue. As an alternative, you can migrate to an acceptable image; preferably, this would be an updated and compliant image. If the Iron Bank base image becomes non-compliant due to End of Life (EoL), for example, you should switch to an updated base image with an appropriate Acceptance Baseline Criteria and Overall Risk Assessment score.
Typically, there is a substantial overlap (such as 6-12 months) between when a new base image is introduced and when the previous version becomes EoL. As a best practice, application developers should check for updated image versions monthly (at minimum) and transition to the new releases. This will improve application security and ensure government compliance.
What is End of Life (EoL)?
A container with an End of Life designation will no longer be supported or updated by the image owner. Iron Bank containers marked EoL are less likely to be approved for Game Warden platform deployments. The image below displays an example container which has been EoL.
The image below displays an example container which has been marked EoL.
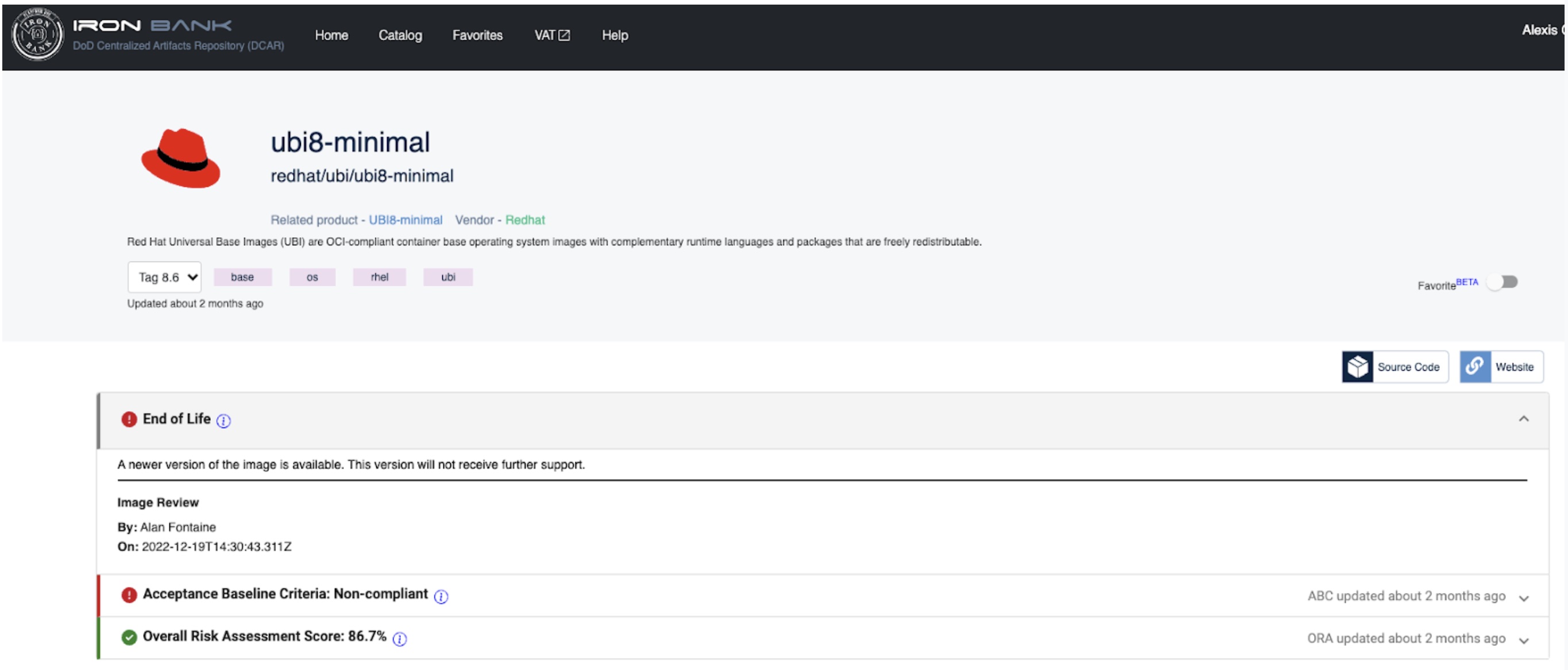
Pulling Containers from Iron Bank¶
To pull containers from Iron Bank (or if your application is not built on an Iron Bank-approved base image):
- Log in to the Iron Bank Hardened Containers Catalog.
You will need to create a Platform One SSO if you do not have this credential. -
Use Search to locate your preferred image in the Catalog.
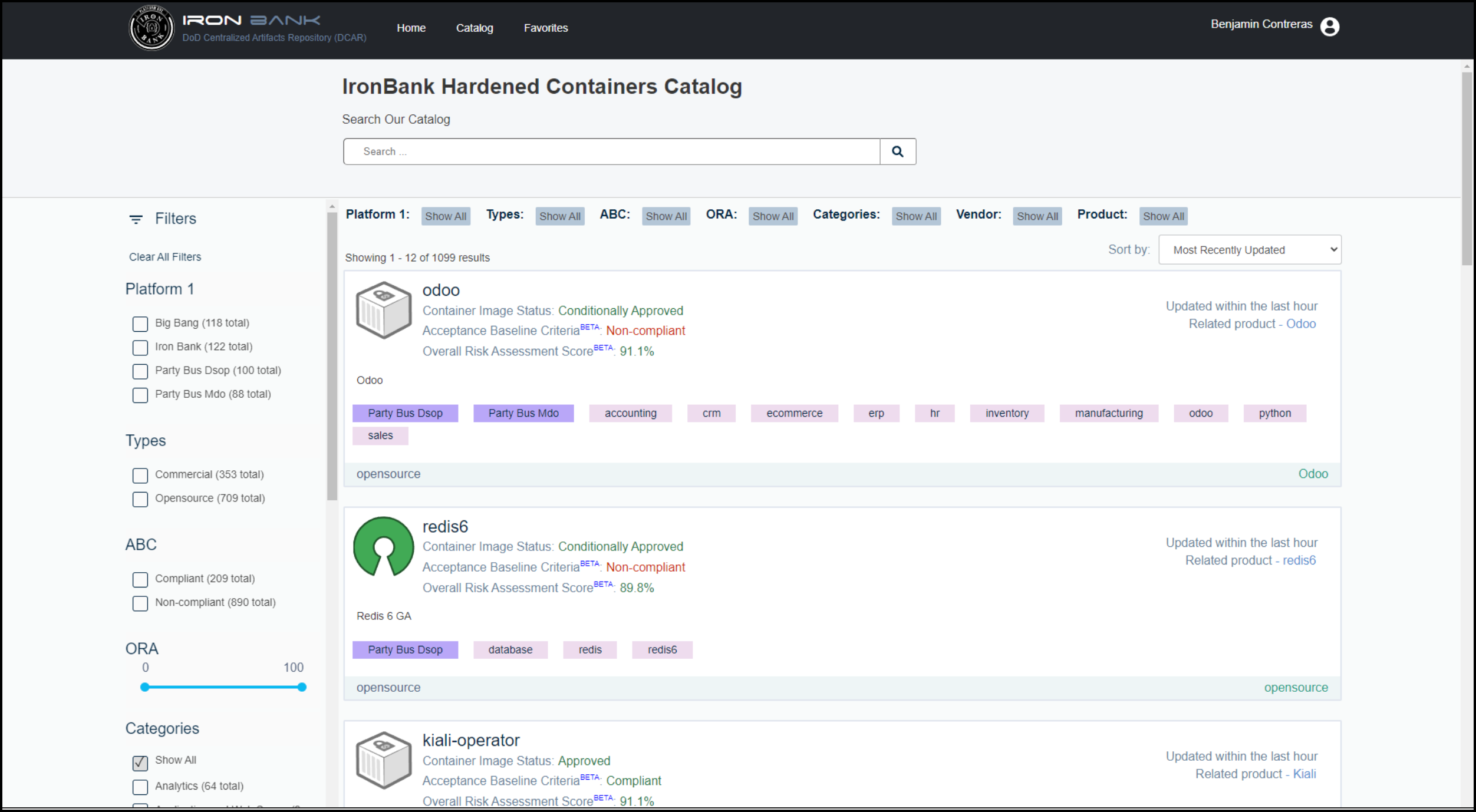
-
Click this image to access the Registry One Docker Pull Command.
-
In the example below, the Docker pull command appears as:
docker pull registry1.dso.mil/ironbank/big-bang/argocd:v2.4.7`
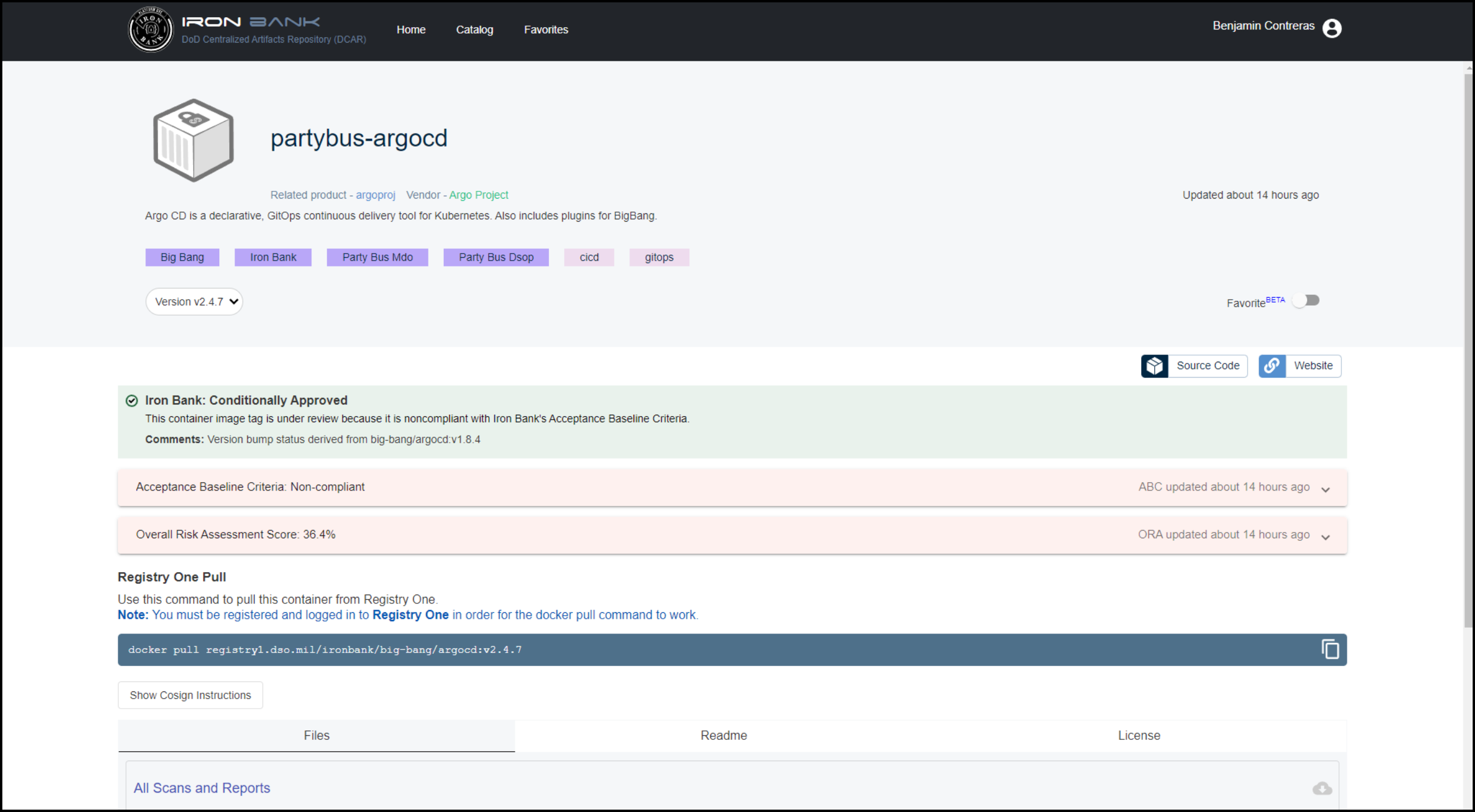
Note
You must be registered and logged in to Registry One for the Docker pull command to work.
Iron Bank Frequently Asked Questions¶
Why can't I select "Inherited from Base" as a justification?
Starting in 2025, our security processes have been updated, and we no longer accept "Inherited from Base" as a justification. This change ensures that all security decisions are made with clear, specific reasoning based on current requirements, rather than relying on inherited settings. As a result, you will need to provide a justification that is directly relevant to your specific security configuration. This update helps strengthen our security posture and ensures that all security settings are appropriately reviewed and documented.
What has changed with this relationship and why are we no longer allowed to Inherit from IronBank?
These images are copied from the software provider, and then maintained and updated by the DoD, which normally lags behind the updates from the maintainers of those images. If a change is required or a CVE is identified, the DoD maintainers must review and republish to Iron Bank meaning that Iron Bank images are often several versions behind the commercially available container. While they are hardened to DoD standards, they routinely have CVEs that require DoD updates and resolution.
How long do we have to make these changes?
Starting now, new deployments and major changes that require a new deployment passport or CtF may not use the “inherited from base” justification to resolve CVEs.
This is a big refactoring change for us, what are our options and will we be pulled from production??
ScanLab will track and require CVEs to be resolved in accordance with DoD Acceptable Baseline Criteria timelines. Applications that exceed these guidelines are identified to our Authorizing Official and may be pulled from production based on estimated remediation timelines.
Can we still use Iron Bank images?
Yes, but all CVEs must still be resolved and the justification “inherited from base image” will not be accepted as a resolution. For example, a CVE may exist but only be exploitable under certain conditions, or if deployed in combination with dependencies that are not included in the application, or can be removed. As IronBank images are managed by the US Government, full remediation will likely require forking the image into a custom container which is then assessed by 2F as a custom container.
How do we manage End of Life Iron Bank images? These images become EOL suddenly.
Unfortunately, Second Front has no control over EOL determination for containers, and we receive no warning or updates on this decision from the IronBank team. This can create unforeseen delays during the security review process if containers are marked EOL then identified during assessment. Ironbank containers that are marked EOL will not be approved for deployment and must be updated to an active image. Alternative options include using Chainguard images through Second Front’s partnership.
Are there any use cases where EOL images may be used?
Vulnerability statuses of EOL containers are not inheritable, and use of EOL containers should be avoided. As a rule, Second Front will not deploy applications that have EOL container images since our Authorizing Official won’t accept them. If no updated versions are available, the customer must provide strong justification for continued use, including an endorsement from the mission owner, which must be approved by the Authorizing Official.
What are the Acceptance Baseline Criteria and Overall Risk Assessment scores that are acceptable?
Current Acceptable Baseline Criteria and mitigation tolerances are listed in the Game Warden Help Center. Containers with an Overall Risk Assessment score of 80% or higher have the highest probability of being approved for use, however these scores may change when CVEs exceed the Acceptance Baseline Criteria timelines.