Government Access Cards¶
You must have a Common Access Card (CAC), External Certification Authority (ECA), or Federal Personal Identity Verification (PIV) card to access Game Warden-hosted applications at Impact Level (IL) 4 or higher. These cards provide access to the Staging (STG) and Production (PRD) environments.
CACs, ECAs, and PIVs are wallet-sized cards and might vary slightly in color and access based on the card holder’s level of government support. You can insert these cards into card readers to gain access to government systems.
You must obtain these cards from government sponsors or a Department of Defense (DoD)-approved third-party vendor, as the Game Warden team has no involvement in the government access card issuance process.
Note
Upon receipt of your government access card (and any applicable certificate downloads), you must configure this card to work with your Platform One (P1) Single Sign-On (SSO)credentials. For additional information, read Government Access Cards and P1 SSO Configuration.
Access Card Options¶
Common Access Cards (CAC)¶
You must navigate the DoD vetting process to secure a CAC from a government sponsor. This process may take months to complete. The DoD issues CACs to eligible DoD active military personnel, reservists, civilians, and contractors.
| Card Type | Process to Acquire CAC |
|---|---|
| CAC | You must work directly with your government sponsor to obtain CACs, navigating: 1. Sponsorship and Eligibility 2. Registration and Enrollment 3. Background Investigation 4. Card Issuance For detailed information, access Process for Acquiring or Renewing CAC or review General Information for additional insight. |
External Certification Authority (ECA)¶
You must navigate the DoD vetting process to secure an ECA from a DoD-approved third party such as IdenTrust or WidePoint. This process may take approximately 30 days to complete. ECAs are alternatives to CACs. The DoD ECA program issues approved certificates to eligible individuals associated with companies who use DoD systems.
| Card Type | Process to Acquire ECA (IdenTrust) |
|---|---|
| ECA (Identrust) | Detailed instructions provided by Identrust can be found here. |
Warning
- The Game Warden team recommends DoD-approved third-party IdenTrust to assist with secure government access. In addition, the Game Warden team recommends ECA Medium Token Assurance, which is an IdenTrust token type that ensures functionality with Game Warden’s Keycloak SSO. This is the Identity and Access Management (IAM) solution that allows you to access the Game Warden Web App, your products, and other Game Warden-hosted solutions more securely and using a single set of login credentials. We have no affiliation with IdenTrust and suggest you contact them directly with any questions.
- Customers using an IdenTrust ECA and a Mac computer with an M1 chip must use a Firefox browser when accessing government systems. IdenTrust is aware of this restriction and is working diligently to address this issue.
- You cannot use Linux/Ubuntu when attempting to retrieve your digital certificate, as these systems are not compatible. IdenTrust recommends MS Windows and Apple Mac machines. For Windows, IdenTrust recommends the MS Edge and Google Chrome browsers. For Macs, IdenTrust recommends Mozilla Firefox. You also should use the latest browser versions. For additional information, read IdenTrust Certificate Compatibility.
Personal Identity Verification (PIV)¶
Federal agencies issue PIV cards to eligible persons to allow secure access to government systems.
Users with CACs, ECAs, or PIVs will have access to the Game Warden IL2, IL4, and IL5 environments via Platform One (P1) SSO, given that their cards are associated with one of the required Certificate Policies. The Game Warden team encourages card holders to contact the Game Warden Platform for proactive guidance, as our team can perform testing to ensure IL2/IL4/IL5 access.
| Card Type | Process to Acquire PIV |
|---|---|
| PIV | You must work directly with your government sponsor to obtain PIV cards. Customers with PIV cards will have access to the Game Warden IL4+ environments, given that their cards are associated with one of the required Certificate Policies. The Game Warden team encourages card holders to contact the Game Warden Platform for proactive guidance, as our team can perform testing to ensure IL4+ access. |
Certificate Policies¶
Below are the certificate policies specific to PKIs. These policies (or rules) are embedded into hardware tokens. Contingent upon the government agency, different certificates may have varying permissions.
Users with CACs, ECAs, or PIVs associated with one of the required certificate policies listed below will have access to the Game Warden IL2, IL4, and IL5 environments via P1 SSO, as these policies identify them as trusted system users.
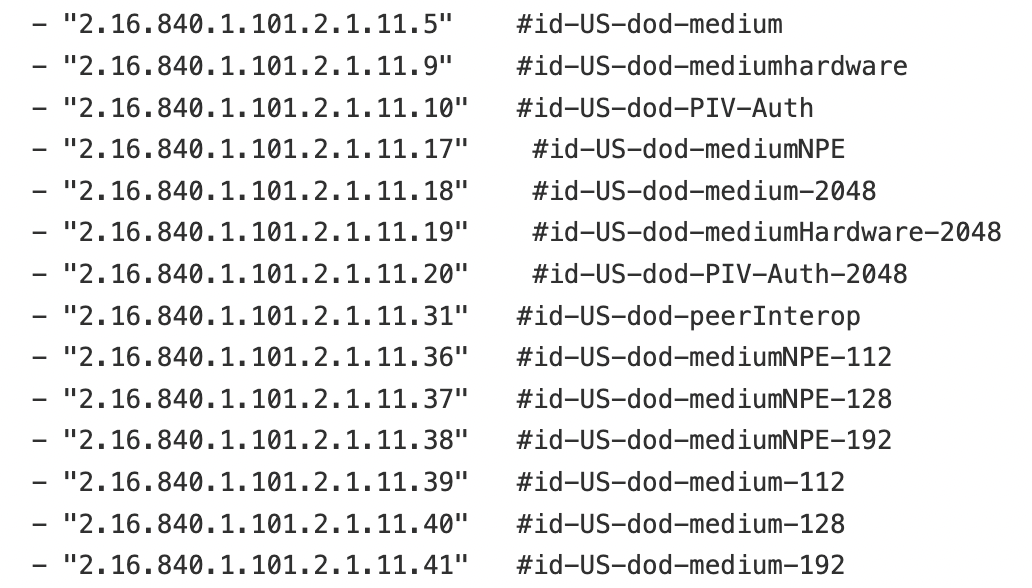
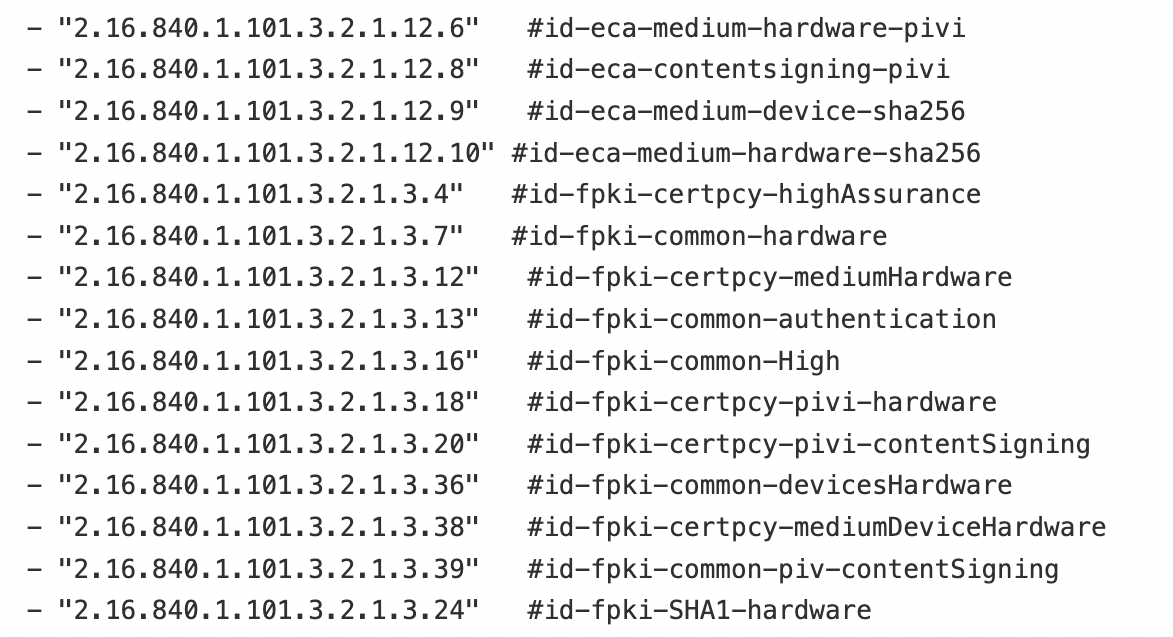
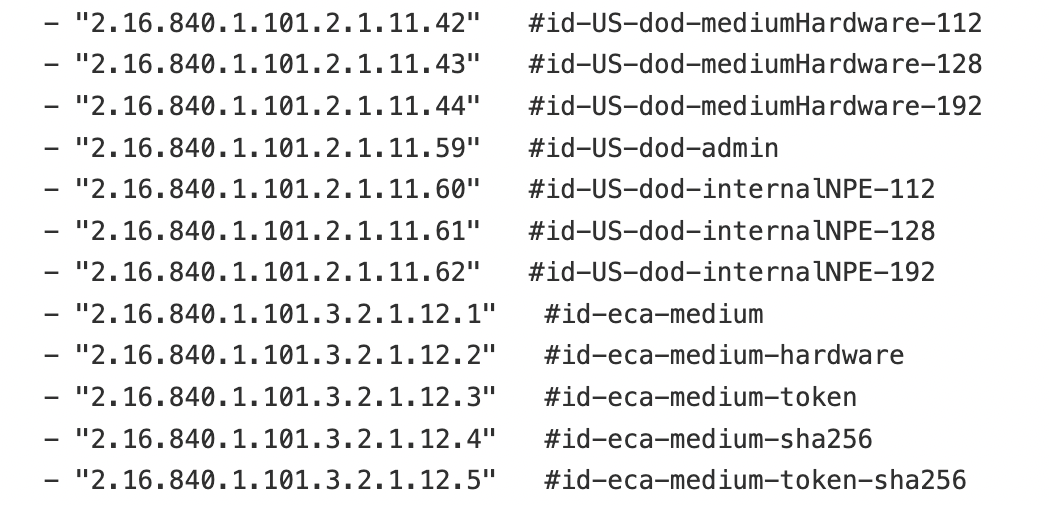
Government Access Card Comparisons¶
The tables below provide general requirements along with the acquisition process for each card type. While government sponsors issue both CACs and PIVs, you must secure ECAs from the DoD-approved vendor, IdenTrust, Inc.
Each card provides access to government systems. CACs, ECAs, and PIVs provide access to IL4+ environments.
General Information¶
| Card Type | Wait Time | US Citizenship | Cost |
|---|---|---|---|
| CAC | The National Agency Check with Inquiries (NACI), which participates in the Background Investigation, takes up to 18 months to complete this process; however, you might be issued a CAC if fingerprint results are acceptable. If NACI does not approve card issuance, this agency will revoke the previously issued CAC. | Not Required | Consult with your government sponsor. |
| ECA (IdenTrust) | After form completion and notarization, you have 30 calendar days to submit this information to IdenTrust. Information is INVALID if submitted more than 30 calendar days after paperwork notarization. Upon form receipt, IdenTrust will proceed with a verification process which takes 3-5 business days. Certificate shipment is contingent upon the courier you select. | Not Required | Access Current Pricing, Certificates and Vouchers. Prices for Non-US Citizens vary slightly. |
| PIV | 2-6 Weeks | Not Required. Must be a US National | Consult with your government sponsor. |
Private Key Infrastructure
Private Key Infrastructure (PKI) is a security framework that exists in each card and uses encryption and authentication to validate users and provide secure access to government systems.
PKI implementation is widely used and not only exists in CACs, ECAs, and PIVs but also in Web browser security (via Transport Layer Security/TLS and Secure Sockets Layer/SSL) along with bank card microchips. Although PKI is a security framework, CACs, ECAs, PIVs (and other entities that include the PKI encryption and authentication) are often referred to as PKIs.
Initial Setup and Configuration¶
Once you have obtained your Government Access Card, reference this article about Government Access Cards and P1 SSO Configuration for your initial setup.
Frequently Asked Questions¶
FAQ: If I do not have a Government Access Card, how will that affect my app's deployment to IL4+ environments?
Even if you do not have a Government Access Card (CAC, PIV, or ECA), Game Warden can move your app into IL4+ STG and PRD; however, you will not be able to access your app environment, logs, or endpoint without a Government Access Card.
FAQ: Do I need a reader for my Government Access Card?
In order to use AppGate, access IL4+ environments, and use our Observability tools, you will need both a Government Access Card and the applicable reader.
FAQ: How do I set up a password for a Platform One (P1) Single Sign On (SSO) account created using a Common Access Card (CAC)?
- Log in to your account at https://login.dso.mil/ to access your profile.
- Click the Password tab to set a password.
- Click the Authenticator tab to set up Multi-Factor Authentication (MFA).
FAQ: Could I hire a service member with a Government Access Card to do my DevSecOps work, or does that raise conflict of interest concerns?
Respectfully, absolutely not: Hiring a Reservist/Guard member to use their Government Access Card for company actions is not an option and can get the military member in serious trouble for misuse of access.
Feedback
Was this article helpful? Want to see something more?
Please reach out to us here with your feedback.
Last Updated: 01/02/2024