Common Vulnerabilities and Exposures - 101¶
Vulnerabilities are weaknesses in software that can be exploited by attackers to gain unauthorized access to systems or data. Security researchers are constantly discovering new vulnerabilities as software and the threat landscape evolve.
The content below provides insight into security vulnerabilities and compliance policies to include how Game Warden enables streamlining the software development process to meet Authority to Operate (ATO) and Certificate to Field (CtF) requirements - empowering you to quickly deploy software to your Production (PRD) environment.
CVEs and Department of Defense Environments¶
CVEs (Common Vulnerabilities and Exposures) are important to the Department of Defense (DoD) for several critical reasons: - Cybersecurity Awareness: CVEs provide a standardized way to identify and reference known vulnerabilities in software and hardware. This awareness is crucial for the DoD to understand where potential weaknesses exist within their systems.
-
Prioritization of Remediation Efforts: By tracking CVEs, the DoD can prioritize which vulnerabilities pose the greatest risk and require immediate attention. This helps in allocating resources effectively to mitigate the most severe threats first.
-
Interoperability and Compatibility: The DoD relies on a vast array of interconnected systems and technologies. Knowing about CVEs helps ensure that these systems are compatible and can securely communicate without exposing vulnerabilities to adversaries.
-
Compliance and Regulation: Compliance with cybersecurity standards and regulations is mandatory for the DoD. CVEs play a role in assessing and meeting these requirements, ensuring that the DoD's systems adhere to industry best practices and regulatory guidelines.
-
Risk Management: CVEs assist in risk management by providing a structured way to assess and mitigate vulnerabilities. This proactive approach helps the DoD reduce the likelihood of successful cyberattacks and minimize potential impacts on mission-critical operations.
-
Coordination and Collaboration: CVEs are globally recognized and tracked, facilitating collaboration between the DoD, other government agencies, industry partners, and international allies. This collaboration enhances the overall cybersecurity posture and response capabilities.
Note
Minimizing CVEs in your application is important as a best practice to keep systems secure, but it is mandatory when deploying to US Department of Defense environments.
Info
Common Vulnerabilities and Exposures (CVE’s) are scored by a universal scoring system called the Common Vulnerability Scoring System (CVSS). Once CVEs are scored, they are added to a glossary maintained by the MITRE Corporation, backed by the Department of Homeland Security. CVEs are analyzed by the National Institute of Standards and Technology (NIST), then published on several public sites.
CVEs and Game Warden¶
During your application’s implementation to the Game Warden platform, your containers are scanned for CVEs, with the results populating in Scan Lab - Game Warden’s CVE management hub. Scan Lab provides guidance on vulnerabilities surfaced by our scanning tools and, in most cases, links to patches. You can also remediate or justify your CVEs and request our Security Team’s review all from within the Game Warden app.
After your application is deployed to your production environment, it is scanned daily through Scan Lab, in accordance with the Game Warden Acceptance Baseline Criteria. Any security findings identified by these scans will need remediation/justification within the provided timeframes.
Warning
Failure to submit adequate justification, mitigation (if applicable), or remediation within Acceptance Baseline Criteria timelines will result in delays or the container not being deployed to Game Warden and/or will be considered out of compliance with Game Warden standards.
CVE’s and Scan Lab¶
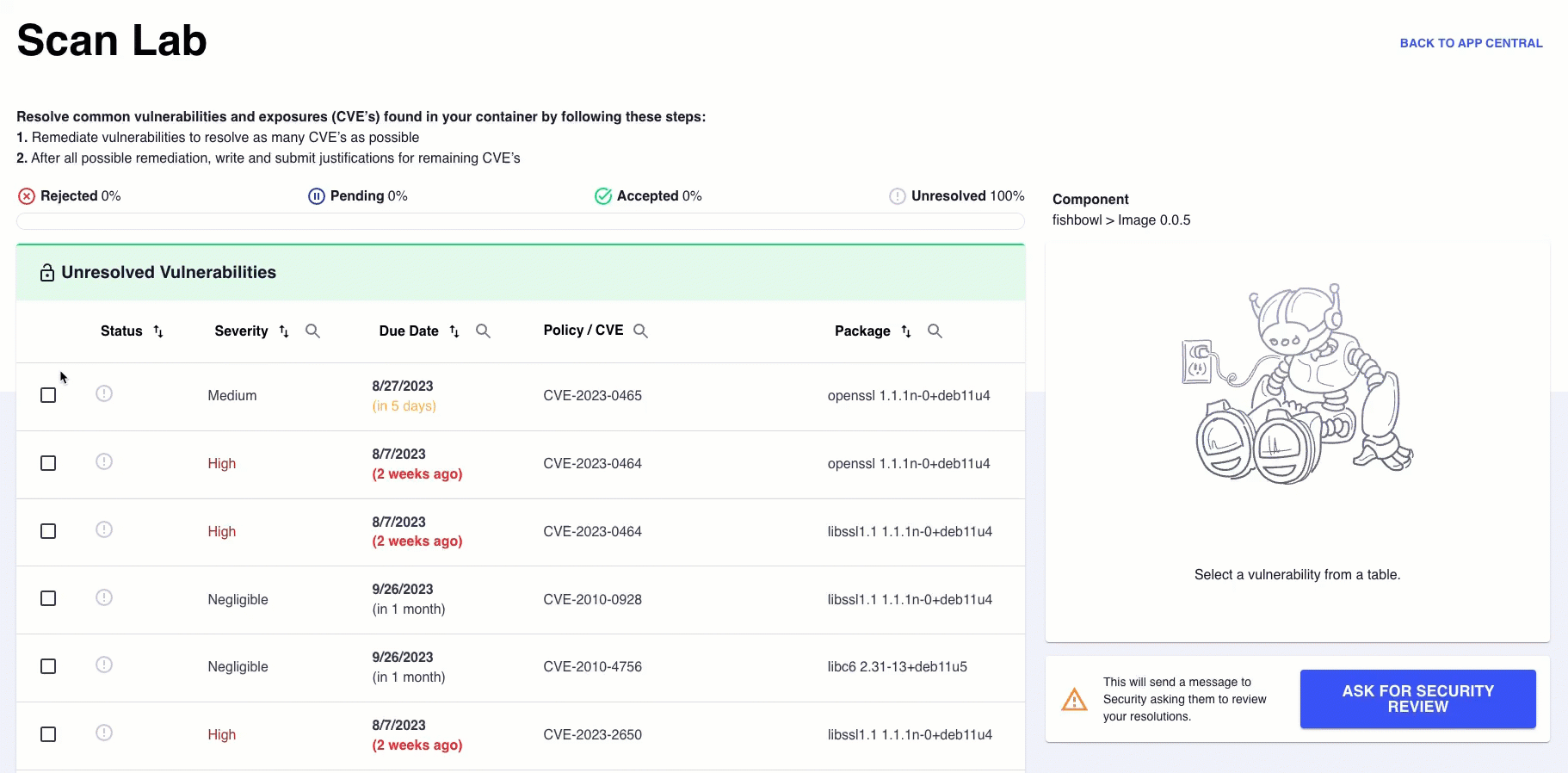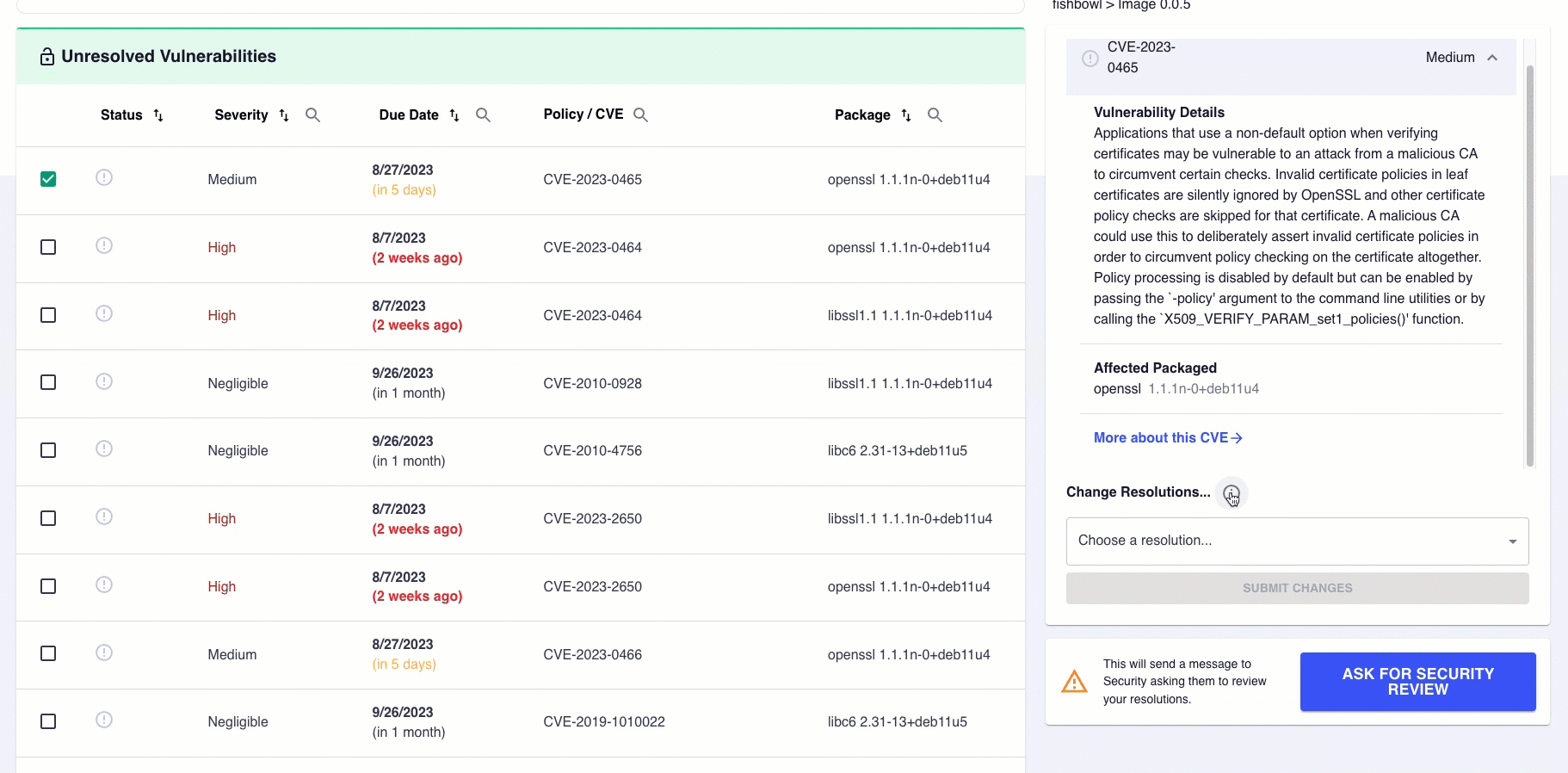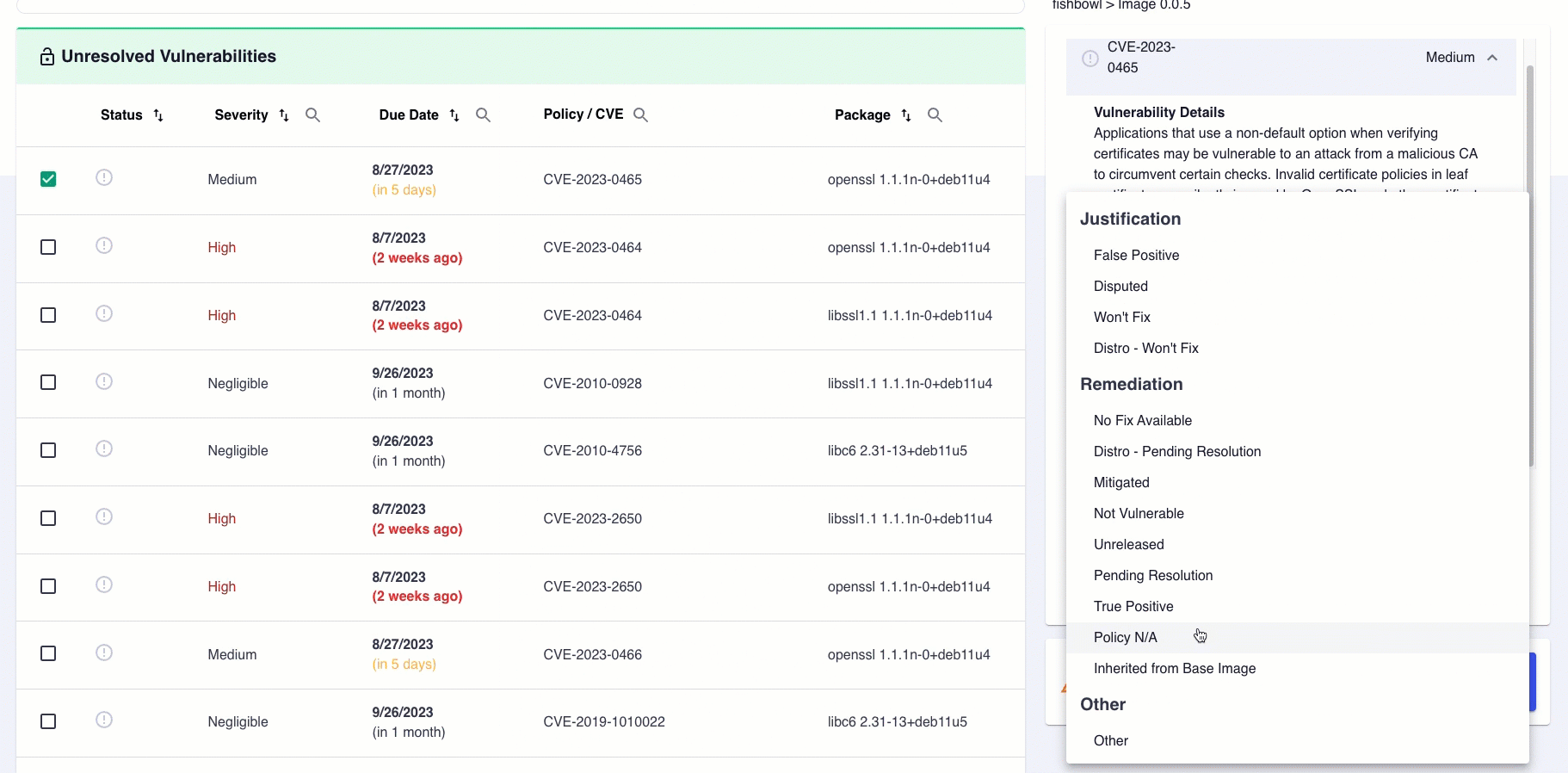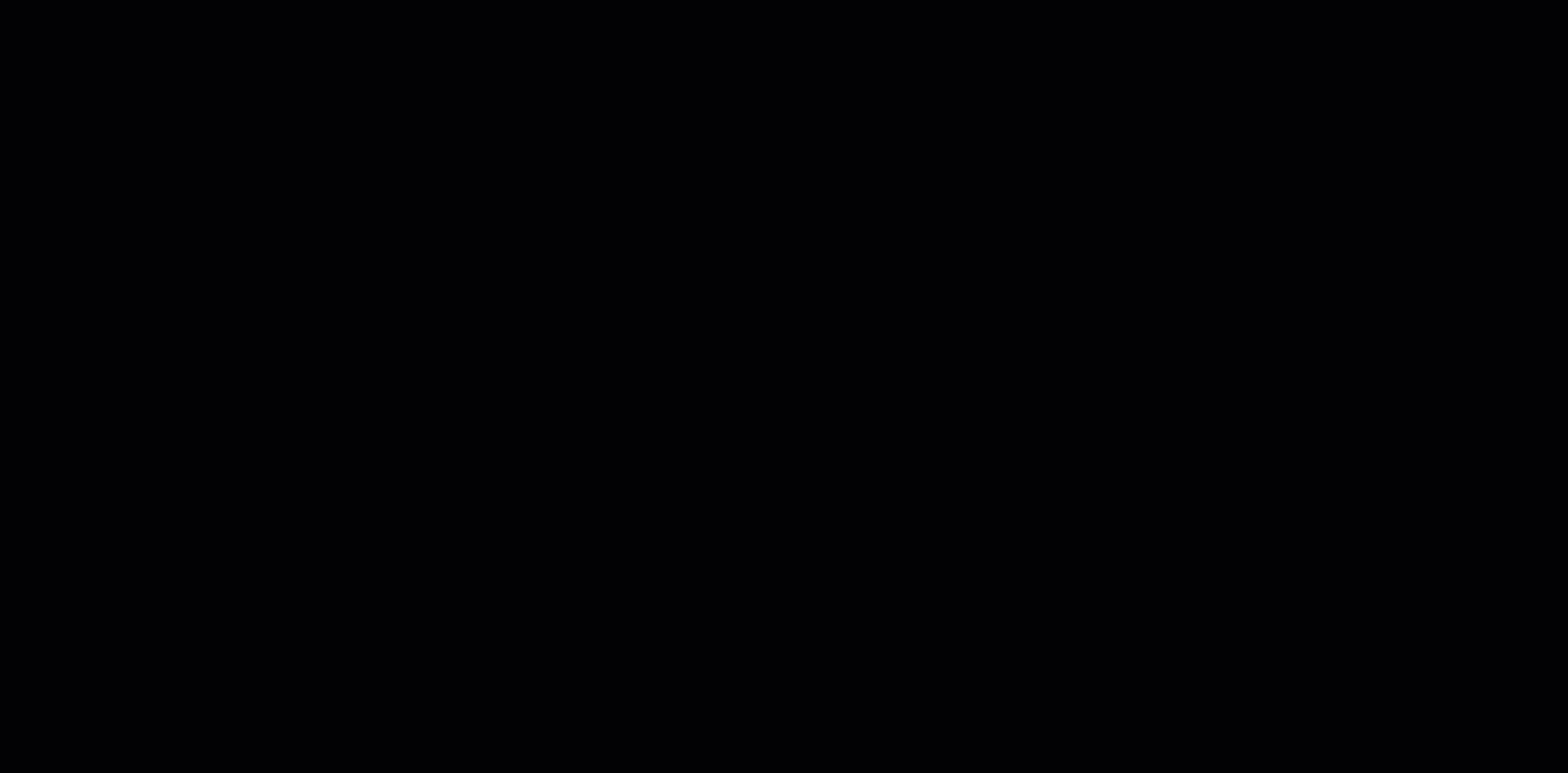
Scan Lab, accessible via App Central, allows you to view Scan Results. You also can resolve or justify Common Vulnerabilities and Exposures (CVEs), address Anchore Compliance Results, and access the Security team's responses to proposed resolutions.
Scan results are organized as line items, each providing the severity level, the due date, the CVE identifier, and the package the CVE was detected in. Each line item also indicates whether the vulnerability is unresolved (exclamation mark), resolved, or new.
Selecting the checkbox for a line item opens a window to the right of the scan results. This window gives details on the vulnerability along with a link to see more information about that CVE. This window also provides a drop-down menu to select a resolution.
Selecting the information bubble above the drop-down menu provides amplifying information on which resolution to select.
Once you have made your selection, you will be prompted to write a comment for elaboration. The more detailed your explanation, the better. When finished, click the SUBMIT CHANGES button to save your progress. Once you save your update, the vulnerability line item you reviewed moves to the Remediations or Justifications list, contingent upon your decision.
Warning
To submit your resolutions to the Game Warden team, you must address ALL security findings for your image. With all findings resolved or justified, you can click the ASK FOR SECURITY REVIEW button. Our Security Team will review and approve or deny your resolutions.
Tip
In ScanLab, sort by “Policy”. This way, you can easily see multiple related CVEs at once to select, bulk edit and submit resolutions.
Info
Go to our Scan Lab and Acceptance Baseline Criteria articles to find information on Scan Results and more.
Free Scanning Tools - Trivy & Anchore¶
Second Front Systems uses Anchore to define policy rules and identify security issues, compliant with NIST 800-53, and complete automated compliance scanning. All compliance findings must be remediated.
The Game Warden platform’s pipelines utilize enterprise versions of Anchore and Trivy to scan your application’s containers for vulnerabilities. If you want to get a preview of your application’s vulnerabilities, you can use the free versions of these tools to scan your containers.
Info
More information on Pipelines and Tooling can be found here.
Note
For information on how to install and run these tools, see the Anchore and Trivy documentation sites.
Anchore Compliance Justifications¶
Anchore compliance results reveal Department of Defense (DoD) compliance issues within an application. Anchore compliance results are based on the National Institute of Standards and Technology (NIST) 800-53 compliance policies required for the DoD. The example below provides insight into a view from the Game Warden Web App. You must remediate or justify these findings as you would remediate or justify standard CVEs. Examples are referenced here.
The compliance result severity types are as follows: - Go – Okay to Proceed, similar to a Low vulnerability.*
-
Warn – Issue a warning, similar to a Medium vulnerability.
-
Stop – Critical error that should stop the deployment by failing the policy evaluation, similar to a High vulnerability.
Warning
*2F requires all vulnerabilities be remediated in all containers unless determined to qualify for a CVE Statement and Memo.
Managing CVE’s Post-Deployment¶
Applications currently in staging or production will be scanned daily. Any new (all) vulnerabilities must be resolved in all containers, to include remediations or mitigations, within the allotted timelines as outlined in Table A and Table B under Acceptance Baseline Criteria.
Note
For more information on Compliance Requirements, please refer to Game Warden’s Acceptance Baseline Criteria.
If a Critical/High vulnerability pops up and remediation is not possible, a new CVE memo is required. Vulnerabilities can and will take place after deploying to production. As the thread landscape changes and new exploits are found, it is pertinent that customers keep their software up-to-date as new CVE’s appear.
CVE Due Dates and New Status¶
CVE due dates will not come into play until after your app has been deployed to production.
We continually scan apps deployed to Game Warden's production environments and sometimes new vulnerabilities are surfaced, hence the New tag that may appear on Scan Lab line items.
This date refers to the Remediation/Justification date in Table A of the Game Warden Acceptance Baseline Criteria and indicates when your team must implement your fixes.
FAQ¶
How do we track down/locate where these vulnerabilities come from?
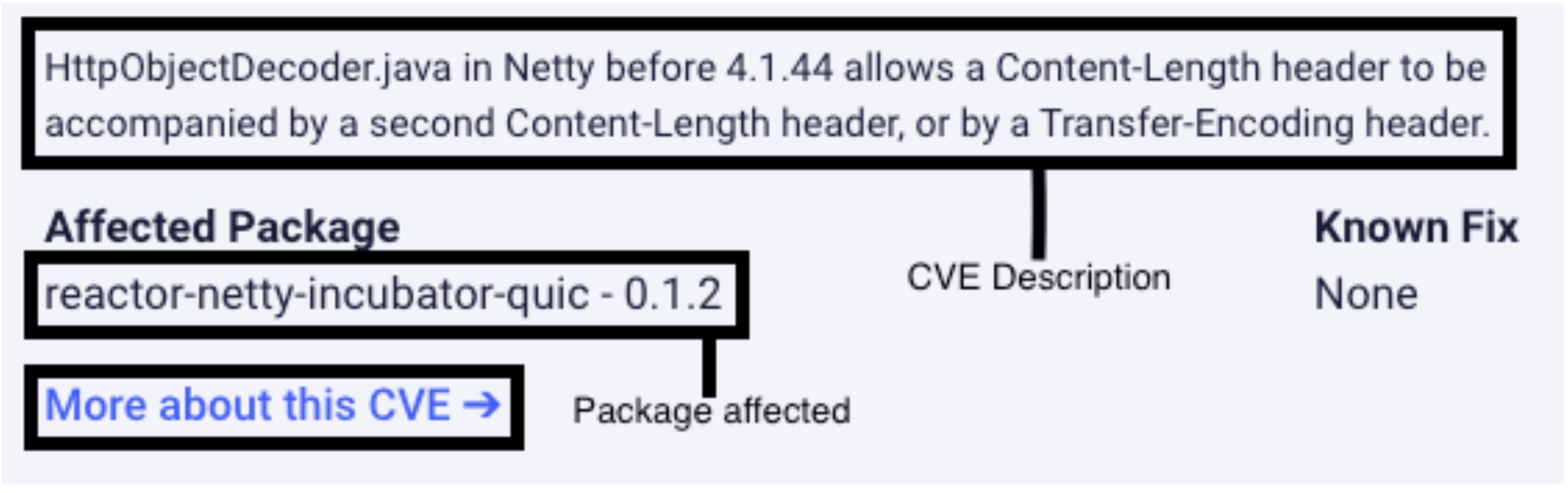
In Scan Lab, when you click on each vulnerability, a side window will pop up containing information “About CVE …” which will contain a link to more information by clicking “More about this CVE →”. This window also includes the Affected Package, which may help you determine whether or not this vulnerability can be fixed.
You can also download the artifacts from your pipeline which contains your csv file of CVEs, as well as a Software Bill of Materials (SBOM) tab to help you pinpoint which package contains the CVE in question.
What is the expectation for medium and low vulnerabilities? Can they wait until we upgrade in a future release?
If pursuing a Deployment Passport, ALL CVE's, regardless of severity, must be resolved. If CVEs are surfaced by routine scanning, Scan Lab will indicate the expected resolution timeline based on Game Warden's Acceptance Baseline Criteria.
What are the SOP’s on running CVE scans/addressing vulnerabilities while awaiting CtF review?
A Code Freeze applies while awaiting CtF review. A Code Freeze is on the customer to adhere to by not pushing new images during this time. Pushing new images will trigger the scans and potentially populate new CVEs in ScanLab, which the customer is responsible for remediation and/or justification. The CtF Review Process will be restarted if there are new CVE’s populated.
Note
If the most recent scan is older than 14 days when Game Warden is ready to run the DAST scan, the Security Team will require a fresh scan, which can result in new CVEs being populated. You may request a new scan by reaching out to your Second Front representative or by updating your image.
If we were to continue deployments to our QA environment for ongoing product testing, would those get scanned for CVEs? Or is scanning turned off during the entire review that we'll have to catch up on after 1 month, for example?
A code freeze should be implemented until you receive your signed CtF. Any new image pushes will trigger the pipelines to scan the new images, potentially populate new CVEs, and will restart the process.
What if I see duplicated CVE's?
First, verify that the suspected duplicate is indeed a duplicate and not just the same CVE found in two different packages.
Example
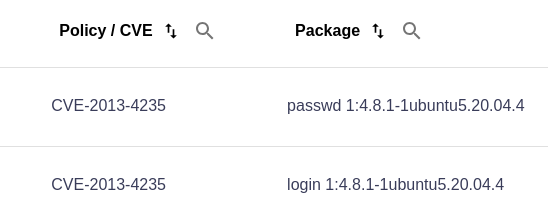
In the image below, CVE-2013-4235 appears twice in Scan Lab but exists in two separate packages. If this is the case, the CVE is not a duplicate and needs to be addressed for both packages.
Note
If this is not the case and the same CVE appears in one package, submit a Support Ticket and our team will address the issue.
What do we do if we can’t upgrade a 3rd-party package that has findings in it?
You will need to justify these findings by explaining why you require this package. You should also note if/when this package will be updated. Your justification will be reviewed by the government ISSM for ‘Critical’ & ‘High’ vulnerabilities, and evaluated by the 2F Cybersecurity Director for Medium and Low vulnerabilities.
Are container scan reports confidential, proprietary, or are any restrictions imposed on sharing scan contents?
You can share scan results with trusted partners, but they need to treat that information as confidential and ensure their POCs do not send to anyone else.
From a sensitivity standpoint, these scans show the exact attack vectors to the applications. In the wrong hands, it is clear to see how that could be risky since your applications are processing sensitive government data.
From a legal standpoint, our Anchore license indicates that as the end user, customers can access and use the read-only scan results. As long as the information is kept close-hold - for example, you directly share it with your technical POC and the access is controlled so it is not shared with anyone else - you are free to do so.