Understanding DoD Impact Levels¶
The Department of Defense (DoD) uses Impact Levels (IL) to classify information systems based on the potential consequences if their data is compromised. This classification ensures that each system has appropriate security measures.
Each Impact Level considers three main security aspects:
- Confidentiality: Ensuring only authorized individuals access the information.
- Integrity: Maintaining the accuracy and trustworthiness of the information.
- Availability: Guaranteeing reliable access to information for authorized users.
The Defense Information Systems Agency (DISA) developed the DoD Cloud Computing Security Requirements Guide (CC SRG) to provide security guidelines for cloud computing. This guide incorporates standards from:
- Federal Information Security Management Act (FISMA)
- National Institute of Standards and Technology (NIST) Special Publication 800-37
The CC SRG extends the FedRAMP framework with enhanced, DoD-specific security controls designed to meet the distinct demands of military and national security systems.
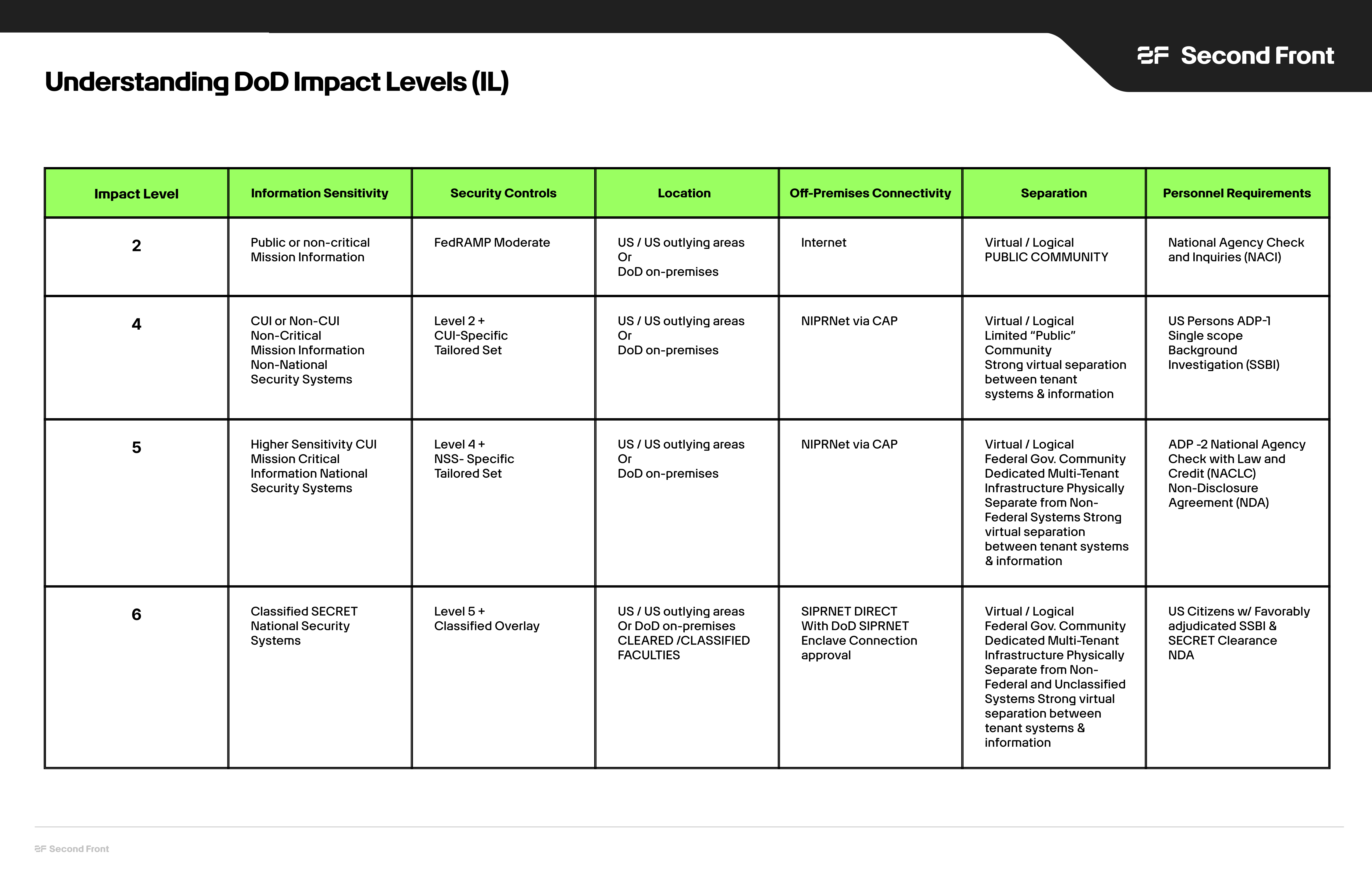
Overview of Impact Levels¶
The DoD defines several Impact Levels, each corresponding to the sensitivity of the data:
- Data Type: Publicly releasable information.
- Use Case: Suitable for systems handling non-sensitive data.
- Data Type: Controlled Unclassified Information (CUI).
- Use Case: Systems requiring protection for sensitive but unclassified data.
- Data Type: Controlled Unclassified Information (CUI) and National Security Systems (NSS) information.
- Use Case: Systems that handle higher sensitivity data needing stricter controls.
- Data Type: Classified information up to SECRET level.
- Use Case: Systems managing classified data with the highest security requirements.
Why Impact Levels matter
If your organization wants to work with the DoD, understanding Impact Levels is essential due to the following reasons:
1. You must match the right security level:
Each DoD project or system requires a certain level of protection. The Impact Level tells you:
- What kind of data you're dealing with (e.g., public, sensitive, or classified).
- What security controls are needed to protect that data.
If your solution doesn't meet the required Impact Level, it can't be used in that environment.
2. It impacts your cloud hosting choices:
Not all cloud platforms are authorized for every Impact Level. For example:
- IL2 can use commercial cloud environments.
- IL5 and IL6 require specially authorized environments.
This affects how and where you can deploy your software.
3. It shapes your compliance path:
The higher the Impact Level, the more security and documentation you need. Knowing your target level early helps you:
- Plan your compliance and certification strategy.
- Avoid surprises later in the authorization process.
4. It builds trust with DoD partners:
Demonstrating that you understand and meet the right Impact Level shows:
- You’re serious about cybersecurity.
- You’re a credible partner for defense work.
Impact Level 5 (IL5) compliance requirements¶
Impact Level 5 (IL5) is designed for systems that manage Controlled Unclassified Information (CUI) with a mission-critical or national security context. These systems require stronger safeguards compared to IL4 environments because they support DoD operations and warfighter missions.
To achieve IL5 authorization, cloud systems must meet stringent criteria, including but not limited to:
- Hosting in a U.S. facility and using a cloud service operated by U.S. citizens.
- Physical and logical separation from non-DoD customers.
- Access controls and auditing that meet or exceed NIST SP 800-53 security controls at the High baseline.
- Continuous monitoring and vulnerability management compliant with DoD standards.
- Incident response and reporting procedures aligned with DoD cyber operations.
These requirements ensure that systems operating at IL5 can protect mission-sensitive data while maintaining availability and resilience. Most commercial cloud offerings require significant customization and investment to meet these demands.
Obtain access to IL5¶
To access an IL5 environment, you must complete a series of prerequisites to ensure your identity, system, and access controls meet DoD security standards.
Begin with Platform One onboarding
- Visit the Platform One site to provision a Platform One (P1) Single Sign-On (SSO) account. See Platform One for detailed instructions.
- Install and configure Appgate SDP, which is required for secure network access. See Install Appgate SDP for detailed instructions.
- Configure your government-issued access card—such as a CAC (Common Access Card), ECA (External Certification Authority), or PIV (Personal Identity Verification)—to map to your P1 SSO account. See Platform One (P1) SSO Configuration for detailed instructions.
- Run compliance hardening scripts on your device to achieve at least 80% compliant before proceeding. See IL5 Access Setup for detailed instructions.
Access and review IL4 documentation
Before gaining IL5 access, you must review critical documentation hosted in an IL4 environment, which outlines compliance expectations for IL5 systems.
As IL4 documentation is hosted within a secure environment, it requires the same access setup completed during Platform One onboarding:
- P1 SSO account
- Appgate SDP
- Mapped government-issued access card (CAC, ECA, or PIV)
Additional configuration
After satisfying the above requirements:
- Our engineering team will ensure you are assigned to the correct application groups.
- Additional access configurations may be required based on your role and project scope.
Need help?
If you have any questions or encounter issues during the process, reach out to our Customer Operations team for assistance.
Game Warden environments¶
Game Warden environments are aligned with DoD Impact Levels and follow a structured deployment lifecycle. Each deployment stage corresponds to a designated Impact Level aligned with the data sensitivity and operational purpose of that environment.
Your application is first deployed to the Development (DEV) environment, hosted at IL2. This environment is used for early configuration, code validation, and basic testing. It is designed for non-classified data and offers relatively open access, including to Game Warden customer engineering teams. Our engineers work with your team here to ensure that the application is properly configured and operational.
After initial onboarding, your application is promoted to the Staging (STG) environment. The Impact Level of the STG environment matches the intended Production (PRD) IL. For example, if your application is destined for IL5 production, your staging environment will also operate at IL5.
This is where extensive testing and verification take place under real-world conditions. Access to STG is more tightly controlled and may be limited depending on classification and mission sensitivity.
Once staging tests are successfully completed, your application is deployed to Production (PRD) at your selected IL (IL4 or IL5). This live environment is accessible to authorized end users and is protected by the full set of controls appropriate to its Impact Level.
Game Warden supports production deployments at IL4 and IL5, with IL6 support on the roadmap. Additional security controls are applied as the Impact Level increases to ensure compliance and operational integrity.
Warning
Access to each environment is restricted based on the user's assigned IL. Only personnel with the appropriate credentials and authorizations can access higher-level environments such as IL5.