External Data Connections¶
External data connections are the vehicles used to join two entities that move or pass data to and from the Game Warden boundary. More specifically, they represent machine-to-machine data transfer either from Game Warden-hosted applications to external-hosted systems or, conversely, from external-hosted systems to Game Warden-hosted applications.
You must use external data connections during Game Warden data transmissions when sending or receiving information.
When establishing external data connections, it is imperative that you have a complete understanding of your data directional flow:
- Egress – Data leaves or exits the Game Warden boundary.
- Ingress – Data enters the Game Warden boundary.
- Bidirectional – Data leaves and enters the Game Warden boundary.
While external data connections are extremely useful when transmitting data to external sources, establishing these entities presents challenges. You must be meticulous when establishing these connections. You must consider countless possibilities relative to ports, safeguards such as firewalls, and application components.
Note
Establishing external data connections includes a range of nuances, and there is no configuration blueprint. You must perform your due diligence by ensuring you understand the directional data flow, relevant ports and corresponding protocols, and encryption as it pertains to the path of your data and its datasource.
External data connections are critical because data must be transmitted to your application via the Internet. The Game Warden team needs to fully understand the ports in use, and how they manage data (ingress or egress) such that there is no data spillage; for example, IL4+ data cannot exist at a lower Impact Level. For any applications accredited at IL4+, data transit across the Game Warden boundary (to/from applications) must align with government requirements. Therefore, our team must understand and view these connections. The Game Warden team must have a complete understanding of your system design to ensure it aligns with Authority to Operate (ATO) requirements. For additional information, read Authorization Boundary Diagram.
Best Practices¶
As you create external data connections:
- Ensure the path from the data to its datasource is encrypted, using data in-transit encryption which protects this data from a potential breach such as unauthorized access.
- Know your port – 443 for example – and the protocol, such as Transmission Control Protocol (TCP). Port 443 is commonly used for data transmission or when performing actions that involve network traffic. TCP is the standard protocol in use with port 443, ensuring secure data transmission.
- Understand your data flow (ingress, egress, or bidirectional).
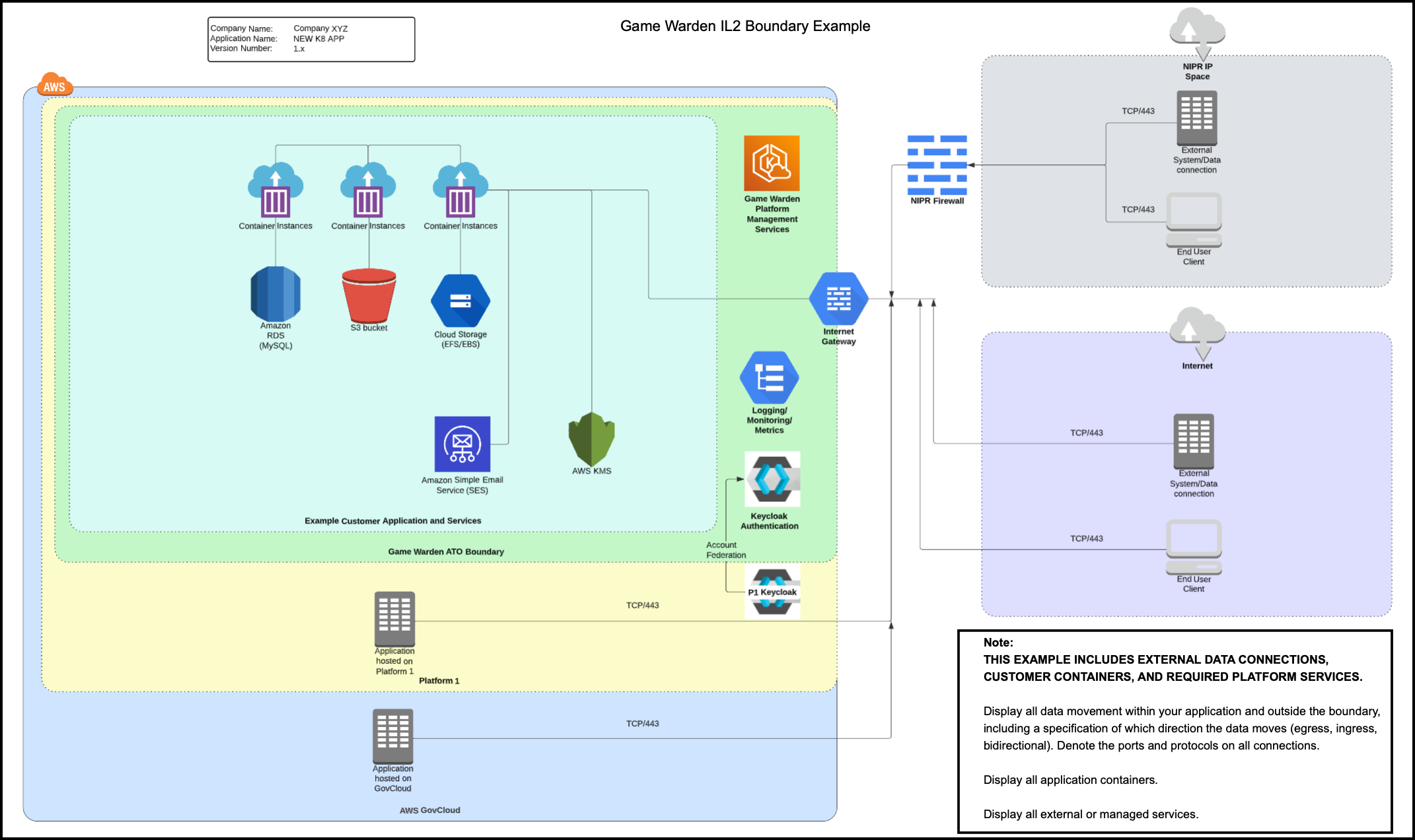
Below is an example IL2 diagram with an external data connection.
This diagram provides a visual presentation of an external data connection, customer containers, and required platform services. When creating your Authorization Boundary Diagram, for example, you must display all data movement within your application and external to this boundary. You must specify data direction (ingress, egress, or bidirectional), and you must denote the ports and protocols on all connections. You also must ensure display of all containers with applications and all external or managed services.
Connection Types¶
Although the Game Warden team is unable to provide a detailed reference guide for establishing external data connections for varied ports, protocols, safeguards, and directional flows, the table below provides general insight specific to Inbound and Outbound connections.
Note
We currently do not support IL6 external data connections.
Inbound Connections¶
| Environment | Movement | Detail/Outcome |
|---|---|---|
| NIPRNet to Game Warden | ||
| From NIPRNet | To Game Warden IL2 | Connects without issue. |
| From NIPRNet | To Game Warden IL4-IL5 | May require Platform One (P1) Cloud Native Access Point (CNAP) whitelisting. For additional information, read CNAP Whitelist. |
| P1 to Game Warden | ||
| From P1 IL2 | To Game Warden IL2 | Connects without issue. |
| From P1 IL4-IL5 | To Game Warden IL4-IL5 | May require P1 CNAP whitelisting. For additional information, read CNAP Whitelist. |
| Internet to Game Warden | ||
| From the Internet | To Game Warden IL2 | Connects without issue. |
| From the Internet | To Game Warden IL4-IL5 | Appgate testing in progress. Currently, this connection is not supported. |
Outbound Connections¶
| Environment | Movement | Detail/Outcome |
|---|---|---|
| Game Warden to NIPRNet | ||
| Game Warden IL2 | To NIPRNet | Recommend submitting a Firewall Exemption Request to the destination system's hosting base. This request should include the source and the destination IP addresses along with any ports used. This information is required to prevent issues with installation or Network Operations Center (NOC)-level firewalls. |
| Game Warden IL4-IL5 | To NIPRNet | Recommend submitting a Firewall Exemption Request to the destination system's hosting base. This request should include the source and the destination IP addresses along with any ports used. This information is required to prevent issues with installation or Network Operations Center (NOC)-level firewalls. |
| Game Warden to P1 | ||
| Game Warden IL2 | To P1 IL2 | Connects without issue. |
| Game Warden IL2 | To P1 IL4-IL5 | Appgate testing in progress. Currently, this connection is not supported. |
| Game Warden IL4-IL5 | To P1 IL2 | Due to cross-domain policies (data transmission from a higher IL to a lower IL for example), this connection type currently is not allowed to prevent Controlled Unclassified Information (CUI) data spillage. |
| Game Warden IL4-IL5 | To P1 IL4-IL5 | May require P1 CNAP whitelisting. For additional information, read CNAP Whitelist. |
| Game Warden to Internet | ||
| Game Warden IL2 | To Internet | Connects without issue. |
| Game Warden IL4-IL5 | To Internet | Due to cross-domain policies (data transmission from a higher IL to a lower IL for example), this connection type currently is not allowed to prevent CUI data spillage. |