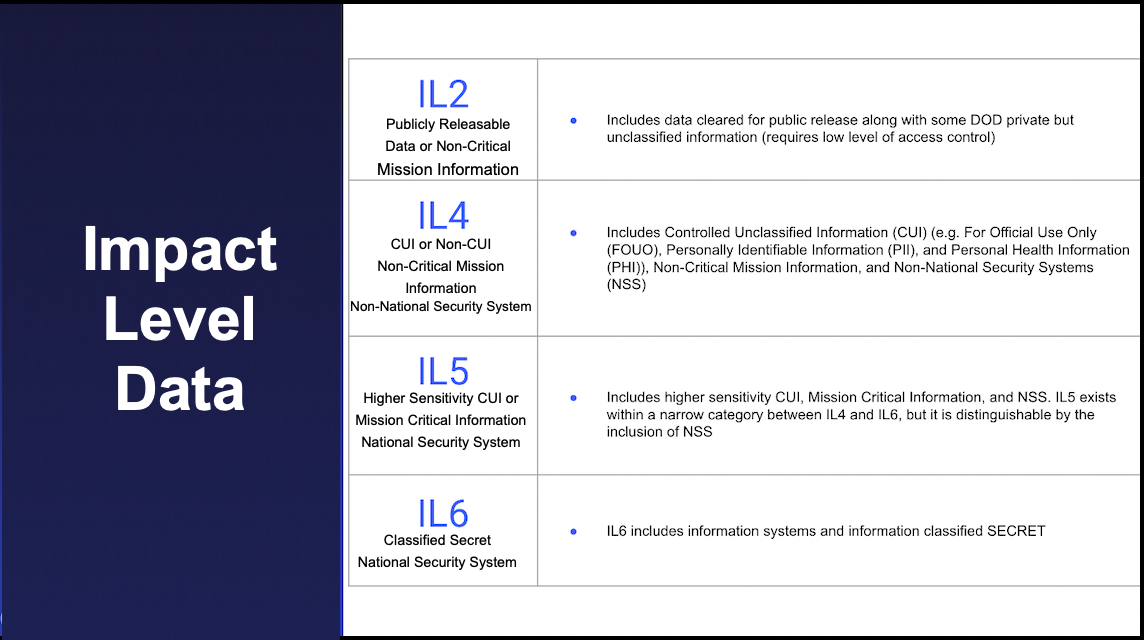
Impact Levels¶
Impact Levels (ILs) are Department of Defense (DoD)-established categories that designate the level of information sensitivity and access. As the numeric value of an IL increases, so does the level of security.
There are four ILs:
Game Warden Environments¶
Development (DEV)¶
Your first deployment is to the Game Warden Development (DEV) environment which is hosted at IL2. DEV IL2 houses non-classified data with generally open access policies. As such, Game Warden customer engineering teams have access to this environment. Our engineers commonly access DEV IL2 to configure the environment and ensure your application functions as designed.
Staging (STG)¶
After the initial stages of onboarding, our engineers deploy your application to the Staging (STG) environment. The IL of the STG environment is contingent upon your intended PRD environment IL - if your goal is to deploy your application to production at IL4, your STG environment will be IL4. Depending on the IL, limited persons may have access to the source code in this environment. In staging, engineers usually perform application-level tasks and, again, must ensure your application continues to function properly. Extensive testing is performed at this juncture.
IL4+ Access
For access to IL4 and higher environments, your team must perform the following: - Obtain a Government Access Card - Download and configure Appgate SDP - For IL5 access, run hardening scripts on your local machine
Production (PRD)¶
Upon testing completion, our engineers deploy your application to the Production (PRD) environment. This is a live environment, accessible to your users, at the IL of your choosing.
The Game Warden engineers can deploy applications to IL4 and IL5 (IL6 is on the roadmap), using additional security controls for higher levels of access.
If you are authorized at the appropriate IL for your endpoint, you should be granted access.
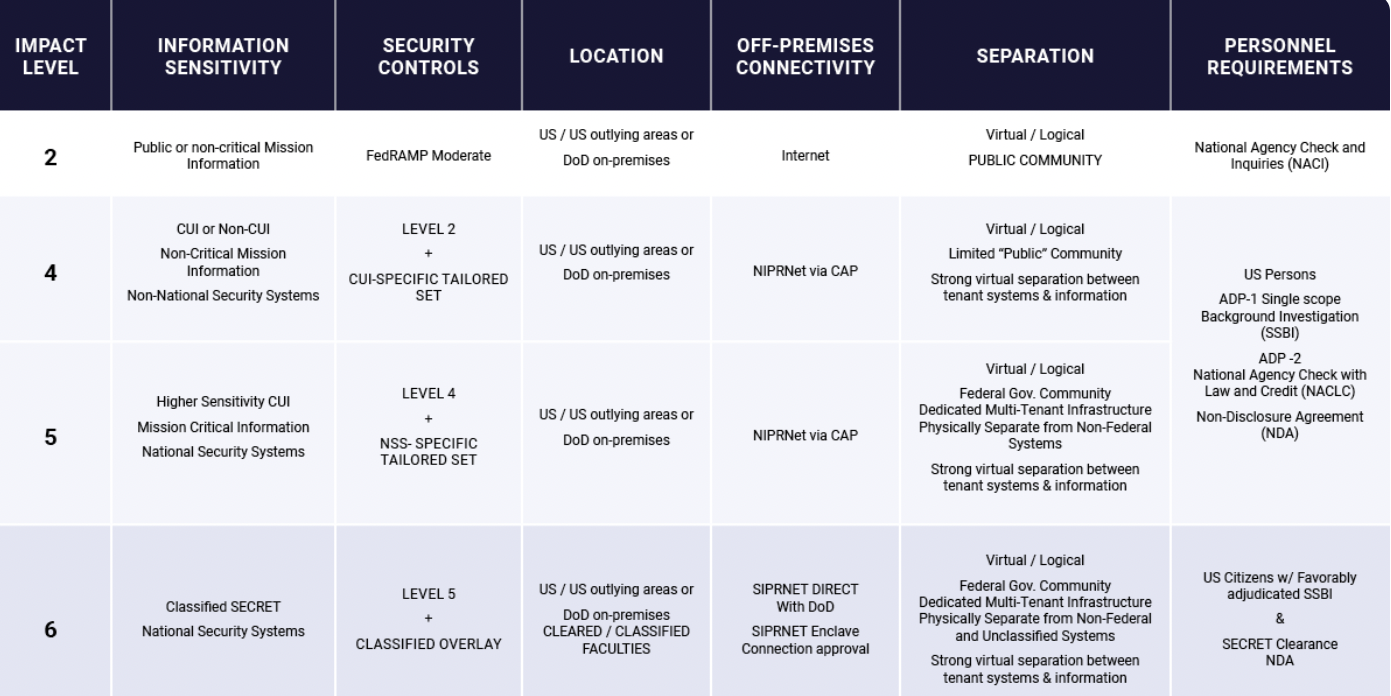
Impact Levels and FedRAMP¶
What is FedRAMP?
FedRAMP is a set of standards cloud providers must follow to gain authorization to work with federal agencies.
How do FedRAMP levels compare to DoD Impact Levels?
"FedRAMP Moderate aligns with DoD Impact Level 2, and FedRAMP High covers 521 of the National Institute of Standards and Technology’s 800-53 security and privacy controls. But IL 4 and 5 go a step further than that in order to meet the DoD’s unique security requirements. IL 5 specifically has an additional 11 requirements from NIST 800-53 above and beyond FedRAMP High, as well as 18 DoD general requirements."
“Achieving ‘the Most Trusted Capability’ for Cloud Service Providers: DOD Impact Level 5.” Federal News Network, 12 Jan. 2022, federalnewsnetwork.com/federal-insights/2022/01/achieving-the-most-trusted-capability-for-cloud-service-providers-dod-impact-level-5/.
FedRAMP also employs "impact levels" to designate security levels cloud service provders (CSP) must meet to be in compliance (FedRAMP Low, Moderate, and High). DoD Impact Levels are used for CSPs that will handle government data.
Data Spillage¶
Data Spillage is the unauthorized process of moving data from a higher IL to a lower one, accidentally, intentionally, or otherwise. More specifically, data spillage involves transferring Classified information or Controlled Unclassified Information (CUI) to an area void of the necessary security to protect this data or information.
Suspected Spillage
If you suspect spillage may have occurred, contact the Game Warden Security team at gamewardensecurity@secondfront.com
Data Spillage Prevention¶
To prevent data spillage:
- Align your actions with the standard protocols for moving data to/from external agencies.
- Do not store sensitive information in shared environments, unless there are security measures in place that solely permit authorized/need-to-know persons with access to these environments.
- Store sensitive data ONLY on authorized information systems.
- Do not breach classification borders.
- Make certain all information recipients have the required clearances/need-to-know access before sending information via email.
- Use Department of Defense (DoD) Secure Access File Exchange (SAFE)/encryption to send Personally Identifiable Information (PII), Protected Health Information (PHI), and other Controlled Unclassified Information (CUI), as required by the DoD.
- Do not store sensitive data on non-sensitive systems.
- ASK if you are uncertain if/how data should be transferred.
Last Updated: 11/20/2023